As the global digital landscape continues to expand, so too do the risks associated with it. The East African (EA) region, while making notable progress in digital transformation, still lags significantly behind more advanced regions like the United Arab Emirates (UAE) in terms of digital infrastructure, cybersecurity readiness, and exposure management.
The East African Region in Context
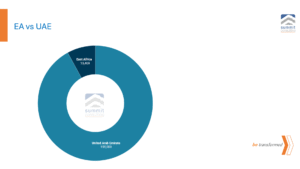
The East African region has approximately 13,409 discovered systems and applications, a figure dramatically lower than the UAE’s 155,000. This disparity highlights the contrasting stages of digital maturity between the regions. The UAE has aggressively invested in smart city projects, e-government services, and a dynamic digital economy, creating an extensive and complex web of digital infrastructure. However, this advancement comes at a cost—broadening the nation’s attack surface and increasing its susceptibility to cyber threats.
Conversely, East Africa is still in the early to middle stages of digital transformation. While Kenya has shown promising growth in its tech ecosystem, countries like Rwanda and Uganda still maintain relatively smaller digital footprints. Uganda, for instance, has recognized the urgency of this challenge by launching a National Cybersecurity Strategy, aimed at fostering a secure and trusted digital economy.
Still, as the digital footprint across East Africa grows, so does its vulnerability. Without significant investments in cybersecurity infrastructure, policies, and talent mirroring models like the UAE, EA countries risk exposing critical systems to increasingly sophisticated cyber threats.
Deep Dive into Uganda’s Cybersecurity Posture
Digital automation has become a top priority in the boardrooms of Uganda’s major sectors, including financial services, telecommunications, utilities, and government. While this shift offers vast benefits in service delivery and efficiency, it also introduces new cybersecurity risks.
A glaring example was the October 2020 cyber breach. Cybercriminals exploited approximately 2,000 mobile SIM cards to compromise Uganda’s mobile money infrastructure. The incident impacted companies like Pegasus Technologies, MTN Uganda, Airtel Uganda, and Bank of Africa, resulting in an estimated loss of UGX 11 billion. This breach laid bare systemic weaknesses in Uganda’s cybersecurity posture, especially in the management of digital payment systems.
Further assessments have identified a host of vulnerabilities within Uganda’s digital environment. Weak cryptographic implementations, unsecured open ports, outdated systems, and poorly configured network access points continue to pose significant threats, particularly to sectors that manage sensitive data.
Exposure Through Open Ports: Uganda’s Top Vulnerabilities
An in-depth analysis of Uganda’s exposed systems revealed 19 critical open ports, many of which are potential entry points for attackers. The table below summarizes key ports and their associated risks:
Table 1: Open ports discovered in Uganda and services running.





