Business Email Compromise

More often than not, corporate emails stand the risk of a sophisticated scam. What exactly does the hacker aim at?
Business Email Compromise is a fraudulent scheme that targets both business and individual emails of an organization through social engineering or computer intrusion to extract personally identifiable information and sensitive data.
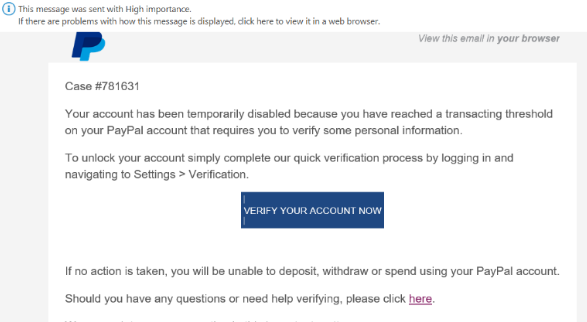
According to the Federal Bureau of Investigation, the phishing scheme continues to grow and evolve, targeting small, medium, and large business and personal transactions. Between May 2018 and July 2019, there was a 100 per cent increase in identified global exposed losses. Some companies reported receiving phishing emails prior to receiving requests for changes to direct deposit accounts. In these cases, multiple employees may receive the same email that contains a spoofed log-in page for an email host. Employees enter their usernames and passwords on the spoofed log-in page, which allows the subject to gather and use employee credentials to access the employees’ personal information.
Scammers from Kenya stole almost $750,000 from UCSD
In the recent past, a group of Kenyan fraudsters scammed the University of California San Diego (UCSD) through a spear-phishing scheme, in which Amil Hassan Raage pleaded guilty to fraudulently receiving almost $750,000.
On July 23, 2018, the University of California San Diego received a spear-phishing email from a fraudulent Dell email account instructing UCSD to redirect its payments meant for Dell equipment and services to Raage’s Wells Fargo bank account in Minnesota, as released by the US Department of Justice on August 1, 2019. Believing that the email was from a legitimate Dell employee, UCSD followed the instructions and redirected payment.
The email actually originated from one of Raage’s co-conspirators in Kenya. From August 8 through September 12, 2018, UCSD sent Raage 28 payments totaling $749,158.37. Each time UCSD wired money to Raage’s account, Raage would promptly withdraw the money or transfer it to another account. When UCSD learned of the fraud, it halted payments.
Phishing activity has gradually escalated while focusing so much on financial institutions, companies, organizations, and universities, among many other targets. This thus calls for increased cybersecurity awareness to cultivate a cybersecurity culture among employees for safe online practices and general cyber hygiene.
Ways to protect your corporate systems
- Use two-factor authentication to verify requests for changes in email account information.
- Beware of hyperlinks that may contain misspellings of the actual domain name. You can first hover over the hyperlink before clicking on it.
- Leverage email warning banners to warn users about the origination of the email (e.g., outside of the organization) or the fact that it contains an attachment. Ensure the URL in emails is associated with the business it claims to be from.
- Use caution when opening emails with attachments. Before opening or risking getting into a Trojan, contact the sender directly and ask if they sent you a file.
- Use antivirus, firewalls and other tools that scan computers and devices regularly to prevent malware infections.
- Do not supply login credentials or Personally Identifiable Information in response to any emails or social media prompts.
- Keep software and operating systems patches updated because hackers exploit known security holes in browsers and operating systems.






Responses