“Dear Mr. Justin Williams, I’m Vikas Manjit Singh from Punjab (India). I belong to a city named Ludhiana. Mr. Williams, I am having a brother in Canada who is also named Justin Williams. He was adopted from my parents by Mr. William Ram of Welland. I and my mum came over to Canada to leave Justin for his new family (William Ram’s Family). It happened in June 1985. So, Mr. Justin Williams, if you are the same person, I’m talking about. Then please give me some time so that I can let you know the realities.”
Imagine what was Justin William was thinking after reading the email. “Who am I? Who are my real parents? What kind of data does Vikas have & know about my parents? Could he be my half-brother”
In reality, this is a scam email originating from a college in Sangroor (India)! Canadian citizens are targeted with such emails. If the targets fall victims, they are asked to send money so that their “brother” can travel to Canada with the proof of the victim’s adoption!
This is just one of the hundreds of email scams being perpetrated on the Internet. These scams are commonly referred to as Nigerian 419 scams. These scam emails are believed to originate from Nigeria and section 419 of the Nigerian Penal Code relates to cheating.
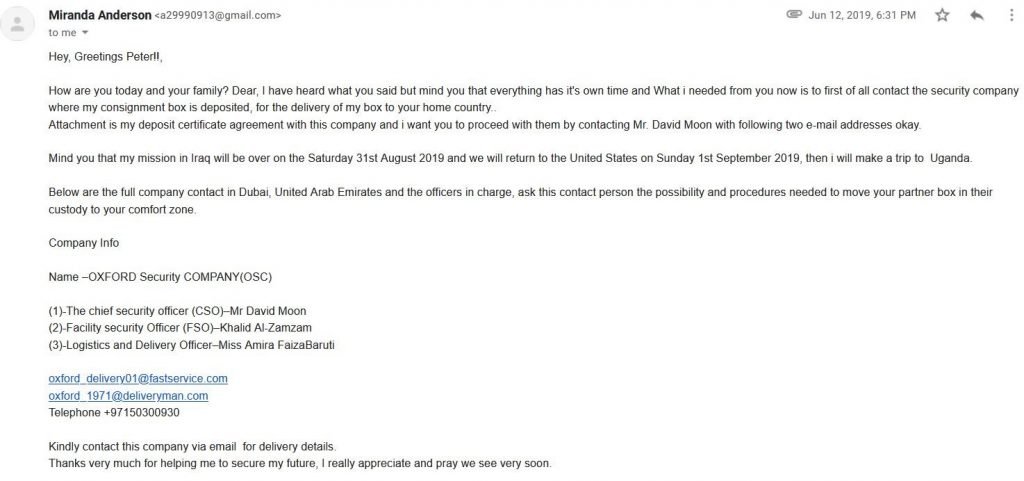
Such email scams usually begin with enticing sentences like “This is to officially acknowledge that the firm has received an authorization letter from your partner Sergeant Miranda Anderson, the US army has been instructing us to dispatch her Trunk Box to your provided Address in Uganda”. The email sender asks the recipient for US$ 2400 to be sent to the courier company so that the consignment (Trunk box) can be sent to the destined country. Another scam email comes with the subject line “Blessed is the hand that giveth”. The sender claims to be a widow on her deathbed. She wants to donate her wealth to someone who will pray for her. Another scam email comes from an “employee of the Euro Lottery”. The “employee” claims to be in a position to carry out a lottery fraud and is willing to share the money with the email recipient.
What is common in all these scams is that scanned versions of official documents are emailed to potential victims. Once the victim is convinced of the genuineness of the transaction, a small fee is requested for meeting bank charges / legal fees/courier charges, etc. It is this small fee that is the motive behind the scam.

Emails are an effective initial infection vector because the targets have email addresses and are easy to find online. The sheer volume of emails means that an employee has only a short amount of time to devote to each one and pulls them into a false sense of security. Cybercriminals take advantage of this in phishing attacks, which have become even more common and effective with the growth of cloud-based email.
Why is this serious?

Did you know that there are over 4.15 billion daily email users as of 2021 globally?
Email is considered a huge medium of communication for organizations across the globe. It allows businesses to maintain contact with their customers and staff. However, over 90% of attacks on businesses start from malicious emails. Cybercriminals send enticing emails targeting specific staff of the organization. If the staff fall victim, the cyber criminals obtain sensitive information like credentials to be authenticated and access key data from the target organization. It is at this point cybercriminals exploit human vulnerabilities, to their advantage.
It is important for organizations not only to rely on built-in security for email. This leaves your organization open to cybercriminals that constantly capitalize on exploiting human nature through email. It is noticed that the great adoption of cloud computing services has only made it easier for cyber crooks to exploit organizations through email. At Summit Consulting Ltd and the Institute of Forensics & ICT Security, we shall be highlighting some of the common email crime cases to watch out for. Due to client confidentiality, we shall use pseudo names and make references to international cases, where possible.
In the following cybercrime series, we shall highlight actual cases with real victims. In this first case, we highlight how cybercriminals lure victims into providing sensitive information through email scams and monetize it.
The Issue (What happened?);

In 2005, an Indian businessman received an email that seemed to be coming from the Vice President of a major African bank offering him a lucrative contract in return for a kickback of Rs 1 million. The businessman had many telephone conversations with the sender of the email. He also verified the email address of the ‘Vice President’ from the Bank’s website and subsequently wired the money to the bank account mentioned in the email. It later turned out that the email was a spoofed one and was sent by an Indian based in Nigeria.
How the case was handled;
After successfully having transferred the requested sum of money to the specified account details in the email, the businessman through his banker requested confirmation from the Vice President if he had received the money. In his response and a big disappointment to the businessman, the Vice President indicated he did not send any email of such nature and has never received any money. He clarified that the Bank uploads ethical conduct and doesn’t engage in bribery in return for jobs. The businessman had fall victim to email fraud.
The businessman requested the African bank to engage the services of a competent forensics investigator. The investigation revealed that an email fraud regarded as a business email compromise (BEC) was used to perform the crime.
A business email compromise which is also known as an email account compromise (EAC) is regarded as the most financially damaging cybercrimes, given the fact that it exploits the fact that so many enterprises rely on email to conduct business.
The attack vector used; Business Email Compromise
This is a cybercrime that is designed to gain access to critical business information or extract huge sums of money through email-based fraud. It involves phishing emails that use social engineering tactics to attack organizations and trick unsuspecting employees, business partners, and executives into conducting tasks under the guide of legitimate business activity, often appearing to have come from a trusted sender
Attackers send emails that appear to have come from a member of your trusted network. This could be someone in an important position at work, such as the enterprise manager, CFO, CEO, or ED, a business partner, or someone that you otherwise trust. The major aim of the email is to convince the victims of these attempts to reveal critical business or financial information or process a payment request that you would never have done otherwise.
Given the rapid business adoption of cloud sources, more business activity goes online. This creates huge room for cybercriminals to target people in business email compromise attacks. The main aim is to get credentials, steal the identities of legit account users, impersonate email communications between compromised businesses and third parties, such as vendors or customers, to request pending or future payments are redirected to fraudulent bank accounts. Attackers have access to other valuable information including emails of other influential people who might turn out potential targets to phishing campaigns. The successful email account compromise at one business can pivot to multiple victims within an industry.
Lessons to improve your cybersecurity resilience:
- Educate employees about BEC scams, including preventative strategies such as how to identify phishing emails and how to respond to suspected compromises.
- Be careful with what information you share online or on social media. By openly sharing things like pet names, schools you attended, links to family members, and your birthday, you can give a scammer all the information they need to guess your password or answer your security questions.
- IT administrators should Enable security features that block malicious emails, such as anti-phishing and anti-spoofing policies.
- IT administrators should configure Sender Policy Framework, Domain Keys Identified Mail, and Domain-based Message Authentication Reporting and Conformance to prevent spoofing and validate email.
- Don’t click on anything in an unsolicited email or text message asking you to update or verify account information. Look up the company’s phone number on your own (don’t use the one a potential scammer is providing), and call the company to ask if the request is legitimate.
- Carefully examine the email address, URL, and spelling used in any correspondence. Scammers use slight differences to trick your eye and gain your trust.
- Be careful what you download. Never open an email attachment from someone you don’t know, and be wary of email attachments forwarded to you.
- Set up two-factor (or multi-factor) authentication on any account that allows it, and never disable it.
- Verify payment and purchase requests in person if possible or by calling the person to make sure it is legitimate. You should verify any change in the account number or payment procedures with the person making the request.
- Be especially wary if the requestor is pressing you to act quickly.
Conclusion
As businesses adopt cloud resources to scale and tap into the global market, a cybersecurity culture is everyone’s responsibility. At Summit Consulting Ltd, we understand the value of email security to our clients and the implications. We continue to focus on the insights stated above to keep our customers protected. To this end, all our customers should take business email compromise threats seriously.
Visit https://www.summitcl.com/free-webinar-on-cybersecurity-hygiene-to-improve-your-security/ to book a free cybersecurity talk to your organization/ employees.
