Healthcare Cybersecurity: Are your medical records safe?

As each day comes, Cyber-attacks and data breaches are increasing in the news and the types of cyber-attacks are becoming more varied and sophisticated. Malicious hackers have developed better ways to evade basic security, they have mastered social engineering, and they have also transitioned from mere petty theft, to information and data theft. That information, may be your medical records that hospitals keep.
Every day, people like you and me place their lives into the hands of healthcare professionals i.e. doctors, nurses and surgeons. But there is another field in which healthcare as a sector in Uganda is severely lacking — cybersecurity. Not only does the healthcare sector lag far behind other sectors when it comes to cyber defense, but it’s also a growing target for hackers and cybercriminals and yet hospitals have the most valuable information – Personal healthcare information (PHI).
You are probably wondering what the endgame of attacking a hospital is, why should you and the medical personnel even care. When a malicious hacker steals data from a hospital, first, they will demand a ransom from the hospital, and risking reputational damage, the hospital has to comply. After exploiting the hospital, the next step is to go through the stolen medical records and find ‘juicy’ victims. These are most likely prominent people in society that care about reputational damage and are wealthy to an extent.
Healthcare cybersecurity statistics
Is it safe to assume that Uganda is the most cyber secure country worldwide? I mean, have you heard of any cybersecurity breaches of late? Or are the hackers in Uganda just less skilled? All that aside, there is a simple explanation; There is little or no regulation regarding cybersecurity and data breaches. Even the data protection and privacy act has not been enforced to compel organizations to report incidents and also give fines and penalties for such organizations.
When you take a look at other countries with regulations like the General Data Protection Regulation (GDPR) and more specifically HIPAA (Health Insurance Portability and Accountability Act of 1996) which is United States legislation that provides data privacy and security provisions for safeguarding medical information, such countries have enormous volumes of statistics as shown below.
a) Data Breaches by year
According to HIPAA, in the years 2009 – 2018 there were 2,546 healthcare data breaches that resulted in the theft/exposure of 189,945,874 healthcare records. That equates to more than 59% of the population of the United States.
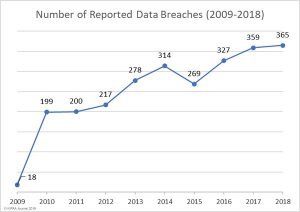
Source: HIPAA
b) Healthcare Records Exposed by Year
HIPAA statistics again show that there has been a general upward trend in the number of records exposed each year, with a colossal increase in 2015. 2015 was the worst year in history for breached healthcare records with more than 113.27 million records exposed.
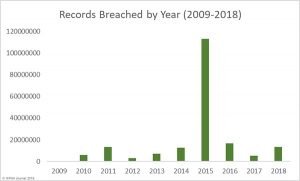
Source: HIPAA
c) Healthcare Hacking Incidents by Year
According to HIPAA, hacking is now the leading cause of healthcare data breaches. Many of the hacking occurrences between 2014-2018 occurred many months, and in some cases years, before they were detected.
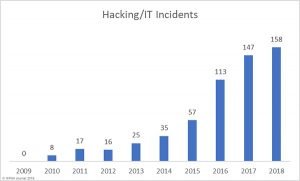
Source: HIPAA
d) Unauthorized Access/Disclosures
The biggest percentage of cybersecurity incidents are rooted in employee negligence. This can occur in any number of ways for example use of weak administrative sign-in credentials, theft of laptops and phones, or maybe phishing attacks where one clicks on a phony email, attachment, link or download, exposing them to malicious software or phishing scams. No matter the reason, it spells big problems for healthcare providers.
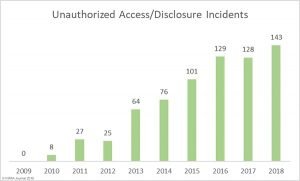
Source: HIPAA
e) Healthcare Ransomware Statistics
Late 2017 and early 2018 were probably the most rampant years in the history of Ransomware. In the past, ransomware has brought many a healthcare organization to a standstill and this trend will most likely continue in the future.
To make matters worse, Healthcare organizations are more willing to pay ransom to avoid downtime and gain access to critical patient data. Healthcare industry is vulnerable because it uses legacy systems that are mostly outdated and vulnerable to attacks.
The next time you visit a hospital check out the Operating systems that their computers are using. The latest you will find is Windows 7, and the most common will be Windows XP. These are Operating systems that are no longer supported and don’t receive security patches.
Impacts of a Data Breach
According to estimates, the loss of data and related failures will cost healthcare companies nearly $6 trillion in damages by 2020 in contrast to $3 trillion, in 2017. If proper security measures are not taken, experts believe that cybercrime can have a devastating financial impact on the healthcare sector in the next four to five years (Source).
At this time, data breaches are costing the U.S. healthcare industry about $6.2 billion per year. In addition to the financial impact a data breach has on an organization, it can also result in a horde of other adverse effects including:
- Business interruption
- Threats to patient safety
- Decrease in trust among customers
- Loss of customers
- Reputational damage
Stopping healthcare cybersecurity threats: Using the right medicine
Cybersecurity threats start and end with the people that are charged with controlling the use and deployment of technologies – the I.T personnel. These people have the ultimate power to create a secure cyber environment and prevent a cyberattack from happening but they are usually lax and hospitals hire untested graduates that passed at university. Such I.T personnel have little or no ideas about cybersecurity apart from the content they crammed to pass university. How else can you explain open wi-fi networks that are in hospitals and these same networks are used to transfer medical information?
Here are a few ways to strengthen cybersecurity in healthcare facilities to prevent future data breaches and cyberattacks.
a) Personnel training and awareness.
You cannot protect what you don’t know. Hospital management needs to get time out of their tight schedules to give training to staff about cybersecurity. Lack of awareness is usually among the lead causes of cybersecurity incidents.
In addition, it’s imperative to have the right cybersecurity team. More than 80% of organizations in Uganda don’t have qualified cybersecurity technicians (they instead have the same old traditional I.T personnel that fix freezing computers and the wi-fi). Cybersecurity professionals can engage in persistent learning and skill-building opportunities to understand how to protect patients, minimize security risk and identity data theft.
b) Proper device security
Device security is important to minimize cybersecurity risks for healthcare facilities. Device security can be maintained the security of these medical devices, it is recommended to keep software updated, set up strong passwords, and to not use the same password for multiple devices. It should also be a policy to make sure the devices are locked or turned off when they aren’t in use. Finally, house data on internal applications and servers, instead of external applications to limit exposure to the outside world.
c) Continuous backups
Healthcare facilities should ensure to have regular ongoing backups preferably to the cloud. This will prevent total shutdown incase a ransomware attacks, data is lost through accidental deletion or any other incidents
d) BCP/DRP Planning
Many hospitals have Business Continuity Plans (BCP) and Disaster Recovery Plans (DRP) that are untried and untested. These plans are developed and left in theory. To make matters worse, there is never a BCP/DRP for cybersecurity incidents. Healthcare facilities need to undertake trainings like http://forensicsinstitute.org/course/business-continuity-plan-disaster-recovery-training/ to set up such plans.





Responses