The Value of an IT Budget to your organization

Your data is valuable and should belong to you!!
But what guarantee do you have that your online records are owned, accessed, and or reviewed by you alone? Yes, you deserve the right to ownership of your personal/and or organizational records, created and processed by you. Nevertheless, our online records are exposed on an almost daily basis, with potentially devastating consequences.
This blog post aims to provide an insight into the value attached to an IT-Budget for an organization by stipulating the impact of being without one in the prevalence of a number of data breaches and hacks that have happened in near recent (2020).
Having company information and personal information is not safe online. Data breaches are on the run almost on a daily basis. Whenever these happen, they leave the sensitive company/individual data exposed. That is; your credit card numbers, email addresses, passwords, social security numbers and sometimes exposing company future plans in company databases. Not forgetting what happened in the Sony hack that left highly sensitive data exposed.
To a great surprise, most people do not understand the gravity of the problem until it personally affects them, when their identity is being stolen for dubious or malicious intent. Though taken lightly, there has been an explosion of more identity-related computer crime where recent studies have it that in every two seconds, there exists a new victim of identity theft.
In regards to the great rise in identity theft attacks, Experian published statistics showing that 31% of data breach victims later have their identity stolen. Not forgetting that the number of exposed records raises much concern and this should raise an alert to data owners more so those whose data is exposed.
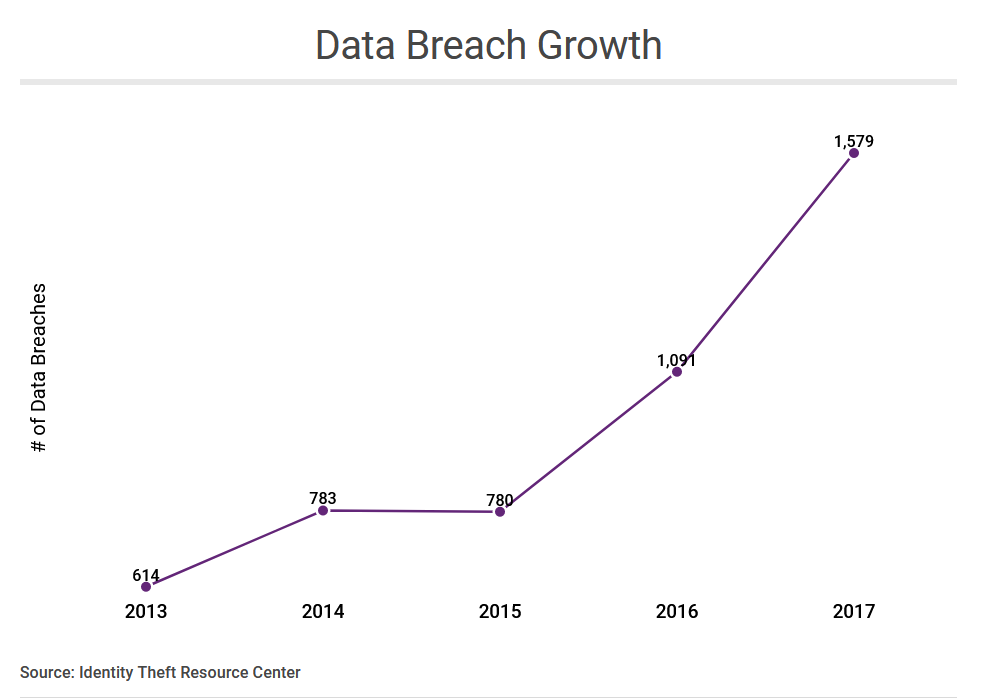
But what is in place for organizations in such a time (pandemic) when organizations are picking up the norm for remote-working, where employees have to register to online platforms like company collaboration tools in order to be productive and participate in their daily activities in the organization. In this way, data breaches become inevitable and unavoidable and we have to understand that the databases whether managed or hosted in the cloud containing the information that we use to create accounts will soon or later be compromised in a data breach.
The implication of an IT Budget in times of a breach.

The IT budget is an operating budget used by an organization to handle issues that fall under the IT sector of the company. In regards to the recent encounters and data breaches, it would take an organization a millage to handle any encounters if at all the organization has an adequate budget that covers the entire IT infrastructure of the organization.
According to the 2019 cyber defense report from CyberEdge, it was notably clear that globally, the mean percentage of the IT budget being allocated to information security currently is 12.5% which raises concern if there is a better way to protect company information when there is no budget or inadequate budget for information security.
There are so many reasons as to why data breaches are successful, some are inevitable and others are as a result of our negligence. Take an example;
Sony Pictures hack

Around 2014 the Sony Pictures company experienced a data breach which was successfully done by the said Guardians of Peace (GOP), who circulated un-released movie, emails (32000 were released in public), password lists and PII (personally Identified Information) of Sony Pictures staff, actors and higher management. The Sony Pictures Hack was successful to the GOP group having penetrated through an unprotected server which helped them to escalate privileges to the rest of the network. It was discovered that Sony Pictures did not have a defense-in-depth approach to their security as there was no basic cybersecurity norm in place, their network was not layered to prevent the data breach to other parts of the network and network devices not well configured as they still had default credentials (username: “username”, password: “password”).
What to note!!
A combination of weak passwords, lack of server hardening, not responding to alerts, or not having the controls in place to set off such alerts, inadequate logging, and monitoring, and lack of Security Education Training and Awareness (SETA) all contributed to the Sony Pictures Breach.
Had there been an adequate IT budget in place, the data breach would not have been as diverse.
In recent days, since so many organizations have failed to realize the relevance of an IT Budget there has been an occurrence of data breaches every other day, organizations being compromised, and sensitive data flooded on the black market.
SELFKEY block-chain digital solutions startup projected that by the time of the report in April 2020, over 8 billion records which included credit card details, home addresses, phone contacts, and other highly sensitive information had been exposed through data breaches since last year. Some of the recent breaches in the recent months according to SELFKEY include;
ExecuPharm, April 27, Nintendo, April 24, 28,000 – GoDaddy, April 23, 5.2 Million – Marriott, March 31, 6.9 Million – The Dutch Government, March 11, all these and more in 2020, – Malicious actors gained access to their critical data and exposed as many critical data as possible through various techniques and vectors.
So these and so many have happened to various organizations, billions of records stolen. that does not mark the end of their happening as many more are coming and others already taking place. It is also mandatory for an organization under a breach to notify the happening of a breach 72hours after occurrence according to the GDPR regulations under (Article 33)
What is advised of an organization in the prevention of a data breach?
Any organization has a mandate to fulfill- which is to ensure that data is adequately protected to prevent loss or theft. In the occurrence of a data breach, organizations to notify data owners (individuals) as well as face a negative impact on the company’s brand and customer loyalty.
It is possible to minimize the risk of data breaches by following a number of best practices:
1. Staff awareness training
Before ensuring IT infrastructure hardening, ensure that you train staff to follow best practices, be aware of the importance of data security, and how to avoid mistakes that could lead to breaches.
2. Software Updates
Ensure auto software updates and that all employees using company IT runs updated and patched software on their devices regularly to avoid weak spots for hackers to exploit.
3. Ensure server and network device hardening
All servers and network assets managed by organizations should be hardened and checked regularly for weak spots, weak passwords, unencrypted data, or weak encryptions through regular security assessments and through network and application penetration testing.
4. Regular Risk Assessments
Carry out vulnerability assessments to review and address any changes or new risks in data protection. Consider all aspects, such as data storage and remote access for employees, and ensure that policies and procedures are adequate.
5. Third-party Data Security Evaluations
Having a third party carry out a risk evaluation allows an objective and outside view of the current breach risks. A Data Security expert can advise on the best solutions specific to each company to reduce the risk of a breach. This also demonstrates a serious intention to ensure data protection.
These and more are adhered to through an IT Budget for which if not considered, it leaves out all that is needed to ensure information security at your organization. We need to find our data the way we left it, but it is still us that reveal our openness and weak spots to those that hunt our data over the internet. So be prepared for the next attack, prepare your IT budget, and make it adequate too!!






Responses