“Your NGO is not losing money through sacks of maize. It is losing it through megabytes of data.”
Most leaders still picture fraud in physical form, missing fuel, fake receipts, ghost beneficiaries, or warehouses half-empty. Yet today’s fraudster doesn’t touch a truck.
He touches a keyboard. Donor dollars vanish quietly, with the click of an “approve” button, authorized by login credentials stolen from the very staff you trust.
NOTICE
Effective 1st October 2025, the technical training arm of Summit Consulting Ltd, the Institute of Forensics and ICT Security (IFIS), has taken the lead as Uganda’s global champion for Cybersecurity Awareness Month. To mark this, we are sharing powerful cybersecurity insights across all our newsletters, bringing cybersecurity to the very center of governance and leadership conversations.
And we are not stopping there. You and your team can now register for a free virtual Cybersecurity Awareness Session worth UGX 5 million, offered at no cost as part of our global Cybersecurity awareness. Simply visit https://event.forensicsinstitute.org/ to secure your slot.
For organizations that prefer in-person training, IFIS is offering on-site sessions at your place of work at a facilitation fee of only UGX 500,000 per team, per session.
Do not gamble with silence. Invest in awareness before a breach forces you to pay in panic. Register today.
The danger is simple: corruption has gone digital, but leadership is still analog.
Boards debate procurement policies while ignoring who controls the server. EXCOs argue over per diem ceilings while the finance portal has no two-factor authentication. Leaders obsess about visibility in the field but remain blind to what happens on the network.
The greatest fraud in NGOs today is not collusion between procurement and stores. It is a collusion between IT and Finance. Why? Because donor funds move electronically, via SWIFT, mobile money, or internal transfers. A single insider can reroute funds to a ghost service provider with no warehouse trail, no physical audit, and no drama.
Other common ways NGOs lose money include:
- Ghost beneficiaries. Hundreds of “recipients” with AI-generated photos and phone numbers. Mobile wallets opened, funds disbursed, activity logged. Paper trail? Fabricated.
- Fake invoices. Suppliers that exist on paper only. Scanned invoices, doctored purchase orders, and bank transfers to shell accounts.
- Inflated procurements. Legitimate vendors collude with program staff to inflate prices; the surplus is siphoned off in cash.
- Payroll ghosts. Phantom staff on the payroll; advances “reconciled” with forged signatures.
- Consultant capture. Phantom consultants submit glossy reports; payments are made up-front, and no deliverables are delivered.
- Cash corridors. Field cash disbursements “recorded” with receipts that match no serials; collectors disappear.
- Collusion with IT. Low-privilege staff climb privileges; approval workflows are bypassed or backdated.
- AI-assisted deception. Deepfakes for IDs, synthetic invoices, convincingly forged emails that pass basic verification.
“Donor dollars are not stolen in sacks. They leak in megabytes.” Hope is not an audit trail. Boards that obsess over petty receipts while ignoring digital controls are writing their own obituary.
Defence is simple in principle, hard in execution: strong segregation of duties, real-time anomaly detection (yes, AI can help), mobile money reconciliations matched to KYC, mandatory forensic spot checks, and a board-level cyber posture that treats prevention as governance.
The Cyber Leakage assessment tool
This is a practical governance tool every NGO EXCO should adopt. It tracks four dimensions:
- Access control: who has the keys to your financial system?
- Transaction monitoring: Are donor dollars matched to verified beneficiaries?
- Data visibility: Can leadership see anomalies in real time, or only in quarterly reports?
- Incident readiness: When, not if, a breach occurs, do you have a tested response plan?
Today’s activity
As part of this month, run a boardroom simulation. Give your managers a scenario: “A hacker has cloned your NGO’s domain email. Donors have received fake invoices with your logo. How do you detect, respond, and reassure donors within 48 hours?” The discussion will reveal gaps in awareness and controls faster than any report.
“Donor confidence is not lost when you are hacked. It is lost when you have no credible answer”, Mr Strategy.
Cybersecurity is no longer about IT departments. It is about leadership survival. If you run an NGO, know this: the future of donor trust lies not in your warehouses but in your WiFi.
Join us this October. Cybersecurity Awareness Month is your chance to shield your NGO from the fraud you cannot see, but cannot afford to ignore.
Board Briefing on Cyber Leakage Readiness vs Target
Donor dollars are stolen in MBs, not in sacks.
Chart 2 below shows your NGO’s cyber leakage readiness against the global best practice target (scale 0–5). While the board routinely debates fuel theft or procurement receipts, the real leakage is invisible, happening in data flows, weak systems, and insider collusion.
Chart 2: Cyber Leakage Readiness vs Target
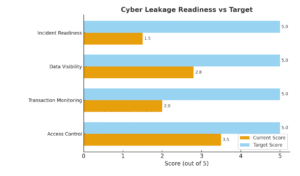
Cyber Leakage Readiness vs Target (Sample data).
- Access Control: 5 vs 5
- Transaction Monitoring: 0 vs 5
- Data Visibility: 8 vs 5
- Incident Readiness: 5 vs 5
Key implications for the board
- There is a trust gap with donors. They assume their money is cyber-secure. Weak scores show a silent erosion of trust. Once lost, donor confidence rarely returns.
- Clear oversight blind spots are visible. Boards focus on warehouse audits, yet digital leakage bypasses those checks. Cyber fraud today requires governance, not just finance oversight.
- At 5 readiness, the NGO is effectively unprepared to respond to a cyber breach. A single spoofed email or fake invoice could cripple operations. This leads to incident paralysis that must be addressed immediately.
- The collusion risk at scale. The weakest links are Transaction Monitoring and Incident Readiness. This is where IT and Finance collude undetected, because the board lacks visibility.
Red flags to look out for
- Staff sharing logins to financial systems.
- Email approvals without multi-factor authentication.
- No real-time visibility of funds-to-beneficiary matching.
- The incident response plan is either untested or non-existent.
Action steps for EXCO and board
- Mandate Cyber Leakage Radar reporting – Require quarterly board dashboards on the four dimensions.
- Close the readiness gap – Prioritize investment in transaction monitoring and incident readiness; treat as a governance survival cost, not IT spend.
- Run boardroom simulations – Test leadership response to donor fraud scenarios. “How do we respond in 48 hours?” should not be theoretical.
- Embed accountability – Assign one EXCO member as cyber risk sponsor. Accountability must be personal, not collective.
“Trust is not lost when you are hacked. Trust is lost when you cannot answer donors with credibility.”
As part of Cybersecurity Awareness Month 2025, Summit Consulting and IFIS will run exclusive simulations and board-level cyber readiness workshops. Your NGO cannot afford to ignore this.
About the IFIS, https://forensicsinstitute.org/about/
At IFIS, we live by our motto, “Discere Faciendo. Learn by Doing.”
Every course, certification, and training session emphasizes practical, hands-on skills that empower you to solve real-world challenges from day one. Learn by doing. Be empowered to transform your career and life.
At the Institute of Forensics & ICT Security (IFIS), we specialize in bridging the gap between knowledge and application. Whether you’re navigating the challenges of cybersecurity, mitigating enterprise risks, investigating fraud, or analyzing complex data, our cutting-edge certifications and practical training programs prepare you to lead in today’s dynamic world.
Come and get skills that you can apply to your job instantly and transform your career and life.
Copyright IFIS 2025. All rights reserved.





