Humankind, not computers, are the pivot region for computer threats. As predators (hackers) victimize others for their gain, access to secure networks is given to predators by humankind knowingly or without know-how, network assets are accessed with the intervention of humankind. Threat actors are unauthorized users who break into computer systems to steal, change or destroy information, often by installing dangerous malware without your knowledge or consent. Their clever tactics and detailed technical knowledge help them access the information you don’t want them to have.
To this knowledge, organizations have worked so hard to protect themselves at the network level through the awareness created and basic cyber norms followed. But still, it is not true that any secure network is 100% secure since it is in operation by humankind which is full of curiosity, knowledge of some security but not exposed to very many techniques. One of the used techniques that are hard to anticipate and protected against are the DNS poisoning technique.
DNS POISONING
This can also be referred to as DNS cache spoofing,
It is a form of hacking technique in which corrupt Domain Name System data is introduced into the DNS resolver’s cache. This causes the Name Server to return incorrect results which are a result of traffic being diverted to the attacker’s computer.
The goal of this attack is to unknowingly redirect Internet users to attacker sites. Hackers use weaknesses of the Domain Name System (DNS) protocol and implementation through the domain name servers.
The DNS protocol implements the mechanisms allowing to make the correspondence between an IP address and the name of the machine (example: www.example.com).
An attacker creates fake DNS entries for the server which may contain malicious content with the same name. For instance, a user types www.microsoft.com, but the user is sent to another fraud site instead of being directed to Microsoft’s servers. The main aim of this kind of attack is to redirect users to fake sites managed by attackers.
In October 2016, many popular websites like Amazon, Twitter, Netflix, and Spotify become unavailable to millions of web users in the United States and to whoever wanted to access them for service, this happened for almost 10 hours. The cause, one of the most powerful attacks of Internet history on Dyn’s DNS services, a major actor in this sector.
Other companies like Google, The New York Times and many banks were also victims of different kinds of attacks aiming at the DNS, the last few years, and if in many companies, the DNS stays forgotten, things are evolving towards awareness forced by these many attacks.
How the Attack is done
If a machine “A” wishes to communicate with a machine “B”, machine “A” needs an IP address of machine “B”. However, “A” has only the name for “B”. So, what happens, “A” will use protocol DNS to get the IP address of “B” from the name.
A DNS request is then sent to a DNS server, declared at the level “A”, requesting the resolution of the name of “B” at its IP address. To identify this request, an identification number is assigned to it. Thus, the DNS server will send the response to this request with the same identification number.
The attack will consist of recovering this identification number by sniffing when the attack is carried out on the same physical network, or by using a flaw of the operating systems or the DNS servers which make these numbers predictable for the ability to send a falsified response before the DNS server.
Thus, machine “A” will use, without knowing it, the IP address of the hacker and not that of the machine “B” initially requested.
Example:
Looking at how DNS poisoning works;
- This can be accomplished using a network sniffing tool.
- Start with ARP poisoning to start DNS poisoning. We will use the DNS spoof plugin which is already there in Ettercap.
- A file etter. dns is edited with the domain defining all domains that you want to spoof. The file contains all entries for DNS addresses that are used by Ettercap to resolve the domain name addresses.
- In this file, we will add a fake entry of “Facebook” “gmail.com”. If someone wants to open Facebook, he will be redirected to the IP address we will put into this file for this specific domain name. To do it, simply open your terminal and type the following command. ~#nano /etc/ettercap/etter.dns
Output

DNS poisoning Attack using a sniffer
Using a network sniffing tool to carry out an ARP Poisoning Attack, the sniffer is set to on a particular network interface of the computer.
A man in the middle attack is initiated in ARP poisoning mode and remote connection sniffing set to on.
Then DNS spoofing is done through managing plugins and invoking the DNS-spoof to send spoofed DNS replies.
The next part is to View Connections and lets the sniffer do the rest.
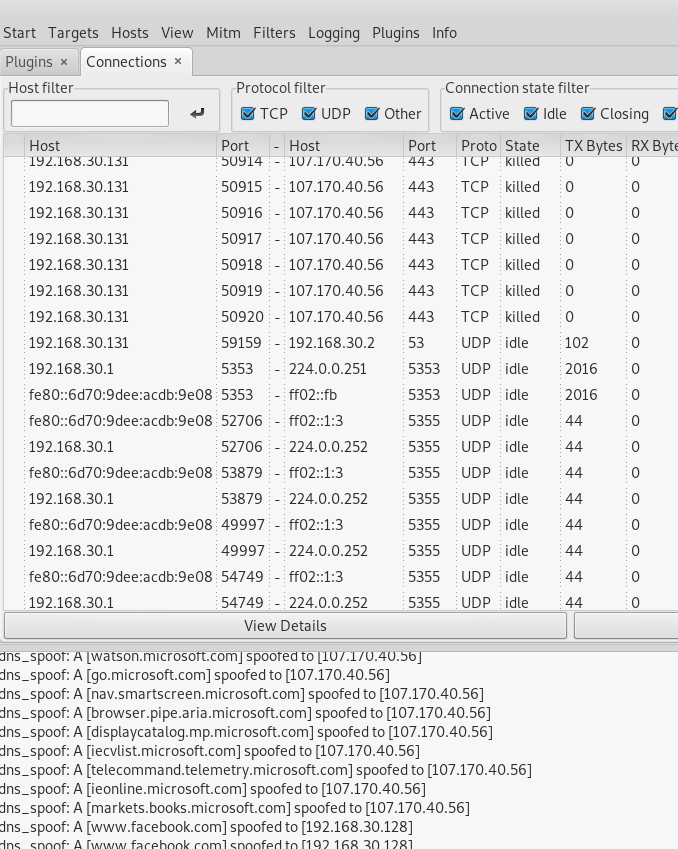
I leave you to imagine what an attacker could do if he cloned the Facebook login page on his server and redirect issues of visitors on it. Or if it came to do the same thing but this time with PayPal or an online payment gateway.
In this quick example, we saw how network traffic can be sniffed through different tools and methods.
How to protect against DNS Poisoning
DNS poisoning is a potential threat to DDoS attacks and this has been witnessed in several case scenarios. Here are defenses against the attacks we just covered from a pen tester’s perspective:
- Update the DNS servers to avoid the predictability of identification numbers and flaws to take control of the server
- Configure the DNS server to resolve directly only machine names of the domain over which it has authority
- Limit the cache and check that it does not keep additional records
- Implement IP DHCP Snooping on switches to prevent ARP poisoning and spoofing attacks.
- Encrypt your sensitive traffic using an encrypting protocol such as SSH or IPsec.
- SSL is a great defense along with IPsec.

