I.T professionals are always responsible for ensuring that the data on the systems they manage is safe beyond a reasonable doubt from the risk of data breaches. They ensure this security through various means for example encryption, use of passwords, setting up network segments, among others. In this article, let us talk about a form of access control that is file system access controls.
File system access controls allow administrators to limit data access to only those users with authorized access. The authority to access files is usually determined using a role matrix of the organization.
All modern file systems provide administrators with a way to control access to files and folders based on the identities of users and user groups. These access control systems allow the simple implementation of an organization’s security policies and adherence to the role matrix in the organization.
The NTFS (New Technology File System) file system, is a proprietary journaling file system developed by Microsoft. Starting with Windows NT 3.1, it is the default file system of the Windows NT family. It is used on Windows servers and workstations and provides a graphical interface that allows file owners to easily add and remove users and groups from file access and modify the access that users and groups have to existing files.
The NTFS file access control is very efficient especially for files stored on the company server and can be easily accessed by anyone in the organization.
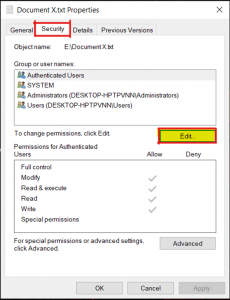
To access the file permissions on Windows-based systems, all you have to do is right-click on any document, then properties, then click the Security tab as shown below;
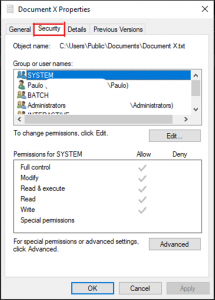
Under the ‘Group or User names’, you can see the users that have permissions to this specific file. NTFS has five basic sets of permissions that may be assigned to users and groups. These include;
Full control. This gives a user complete access of a file or folder and they may perform any action on that file or folder. They can read, execute, delete, modify, take ownership, or change file permissions in other words, they’re in full control.
Read permission. This allows a user to read the contents of a file or list the contents of a folder. Such a user will not be able to delete or modify the contents of the file.
Read & Execute. This has the same permissions as Read above, but goes a step further and also allows users to navigate directories and execute application files.
Write permission allows a user to create files and folders and write data to those files and folders.
Modify is a combination of Read & Execute and Write but it compliments that with the additional ability to delete files.
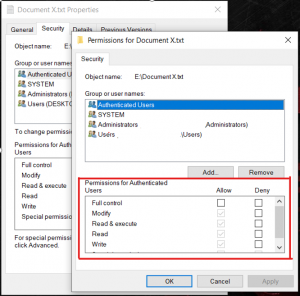
The above permissions can be edited by simply clicking the edit button (see below). After that, permissions can be given as per the user role matrix.