Have you or your organization been a victim of a cyber incident or experienced a data breach? What kind of breach did you encounter? Did attackers steal personally Identifiable information from your sensitive servers? Did they encrypt all your sensitive information and cannot access your systems, or was it an insider that inadvertently exposed the sensitive company information?
Do you have questions about what you should do next or whom to contact if company data was exposed or PII exposed? This article will bring you insights on how to respond to a cyber incident in the digital sphere.
Why care?
The digitally connected environment and its underlying infrastructure are so prone to a range of cyber incidents. These may come as physical and or categorized as cyber threats. The sophistication of the attack varies on the nature of the data or goodies being hunted for. Malicious actors exploit existing vulnerabilities in critical systems to steal sensitive information and or money.
An incident response (IR) is a series of procedures that an organization follows to encounter an attack on its systems. This not only calls for the right technology (hardware and software) but also ensure that they are deployed optimally, configured correctly, and monitored adequately. This gives an organization a better stand to mitigate any cyber-attacks.
A cyber incident is a violation of an explicit or implied security policy. In general, types of activity that are commonly recognized as violating a typical security policy include but are not limited to:
- Attempts (failed or successful) to gain unauthorized access to a corporate system or the sensitive data therein, including PII (Personally Identifiable Information)
- Unwanted disruption or denial of service
- The unauthorized use of a system for processing or storing data
- Changes to system hardware, firmware, or software characteristics without the owner’s knowledge, instruction, or consent
What should Organizations do to stay safe?

As there are growing trends in the magnitude and sophistication of cyber-attacks, organizations must stay ready and prepared to handle the disruptions and damages that any attacks may impose. organizations and individuals need to stay aware of the latest developments in the cybersecurity realm so that they anticipate any malicious intents and prepare accordingly. This is where cyber incident response plans come into play
Your systems are a potential target to cyber-incidents and are at risk of attack. This is not arguably of the possibility of attack but when the attack will happen. However, the aftermath of the attack will vary depending on how quickly and effectively you will handle the matter of securing your critical systems. The whole process calls for cyber-incident Response Preparedness (CIRP).
Get Ready for the Counter-Attack
In the course of an incident, several actions are taken concurrently. The whole process calls for a procedural way of execution to mitigate the cyber incident. Nonetheless, preparing in advance gives an assurance of great outcomes in the mitigation process of a cyber incident. A properly laid Incident Response plan enables the Incident Response Teams to strategically focus on critical areas and reduce further damages, disruptions towards the business-critical systems and or corporate company data
Preparing an Incident Response Plan
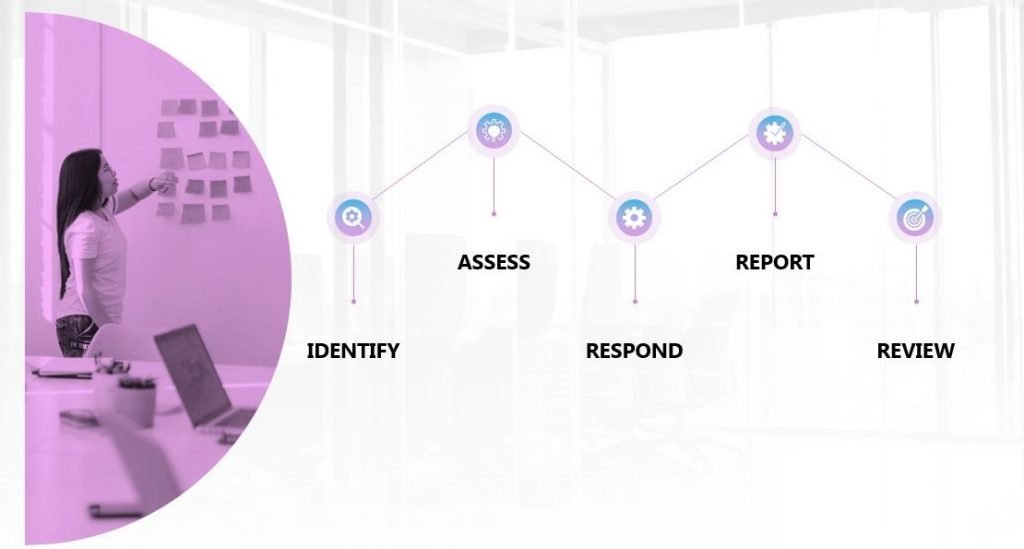
An incident response plan lays down the steps of encountering an attack or any other security issue. Any preparations focused on mitigating any anticipated cyber incidents starts with structuring a plan with all the germane information and procedures that the Incident Response Team (IRT) will follow to mitigate any cyber incident.
Some of the considerations while developing an incident response plan include;
- The appropriate team (Incident Response Team) will steer the incident response process.
- The nature of cyber incidents and the corresponding response.
- Critical corporate data and core systems that require more protection.
- Procedures to coordinate the response team during the times of the Incident.
- Procedures to communicate an incidence to the administrator groups including the stakeholders and the clients (Victims of the breach). It is essential to inform the stakeholders of the business that the organization encounteres a particular cyber-incident. But aslo communicate the status of the mitigation process.
- Procedures to preserve the statuses of affected systems for forensic purposes. This is to protect the evidence from any deterance
Conclusion
At Summit Consulting, we have engaged with so many of our clients while conducting some of the security assessments in regards to IT systems Audit among others, and our findings have it that most firms are not cyber-incident (or disaster) prepared. Overall, an incident response plan like other plans and policies is a requirement.
Download a Copy of a customizable Cybersecurity Incident Response Plan template and improve your preparedness when it comes to the ever-emerging and sophistication of cyber Incidents…

