As organizations traverse the setbacks brought about by COVID-19 and the need to stop its vast spread, many have resorted to a routine of working from home. This comes with many challenges aligned to work ethics, including how to track staff daily working behaviors, tracking ongoing projects, increase productivity, maintaining the focus of staff, and other work-related aspects.
There has been a difficulty in priority for work and home-related concerns like childcare, more time with spouses, more time for leisure with friends and neighbors, lack of work-related tools, and dedicated office space among others.
Of all the aforementioned challenges that the COVID-19 pandemic has increased the risks associated with the disclosure of sensitive company information and many more cyber threats. In this article, we shall be hinting at the security implications that are a result of few employees accessing workplaces and rest working remotely.
Where is the concern?
Cybercrime has been boosted more with the outbreak of the COVID-19. When you hear cybercrime or cybercriminal, the focus is put on a hacker with a hood accessing networks and compromising systems remotely. But it’s not necessarily that attacks have to come from external criminals. We saw according to our summitPROJECT Frontline report that most organizations have weaknesses in their physical security posture. This has been a win-win for malicious actors to access restricted areas of interest in organizations and compromise vital systems from the inside.
As we continually navigate through the pandemic, many offices if not all have gained the status of either being abandoned or fewer employees compared to the normal days. As the numbers lessen, cybercriminals have attack fields clear to get their gold with little hardships. They gain physical access to abandoned offices or those with few staff. With this opportunity, attackers have a clear win to their set social engineering tactics like impersonations (pretending to be legit vendors) to gain access to offices in such times or pretending to be staff at the next office looking for help.
When malicious people gain access to abandoned or sparsely staffed offices, they have all the time to identify weak spots on the network. They locate abandoned office rooms with computers, identify restricted areas like server rooms, and locate poorly secured points like network ports. With identified poorly secured points, attackers use a variety of tools to bypass locking mechanisms.
Some of the tricks that criminals are using to take advantage of the situation
Ring doorbell
In recent days as we progress with the pandemic, I was handling a client project onsite at the office head offices where our company was tasked to conduct a penetration test assessment. As part of the assessment, I had to conduct a physical security review. I posed as though I had come to meet the project coordinator in the organization who was the IT admin. I had earlier talked to him and ascertained that he was working remotely that day.
The client’s office would typically have over 100 people during the normal workday, but because of the high infection rate onsite, they adopted a work-from-home policy. By the time I got to the client’s office, there were probably only close to ten people at the office. I ran into the reception and the receptionist seemed busy on phone, and this gave me a go-ahead to other parts of the office. To my surprise, I came across many open and abandoned rooms in the office. An employee bumped into me in the corridors walking like I knew where I was headed. I didn’t even say anything to him before he moved to the next open room leaving his office open and computer on. He had a puzzled look on his face and seemed so caught up with work than being concerned about verifying a non-staff in the office. He let me move my way into the building.
Sometimes physical security is compromised that easily!
How to protect your physical offices from cybercriminals even in your absence.
Imagine what an attacker can do if they have access to your location now, most especially when the office is abandoned or when a few staff are busy with their work at the premises. A malicious attacker would have plenty of options. These would include; stealing office equipment that contains sensitive company information. Locate network access ports from which an attacker connects rogue devices that act as remote access to the network. Enter unlocked or abandoned office rooms, and log in on unprotected devices (computers with no passwords or even crack the passwords to access data. ). Access restricted areas like server rooms since sparsely staffed offices may pay less attention to who accessed a room, and or may not have real-time monitoring systems for malicious activity or the presence of someone in the room.
While all this is possible during the times of the pandemic, attackers may do something more malicious which is unanticipated by the organization. Attackers may install ransomware on the entire architecture which would deny any employee access to work-related applications.
You should focus on the following to protect your office location from malicious activity;
- Employee security education; Cybersecurity Awareness education is the no. 1 defense mechanism if organizations must combat cyber events. Even when employees are educated about the common attacks and social engineering techniques of phishing, baiting, malicious sites, etc, they may not know how to handle social engineers physically when they appear at office premises. Staff are so essential and will always be the weak link.

Organizations must provide regular training on how to remain resilient and introducing security cultures to combat cyber events. Among some of the key issues to address are;
- Good password hygiene. Staff should not lack a password on any of their technology devices. They should use easy to remember (like passphrases) but hard to crack (complex) passwords and should also enable multi-factor authentication where possible.
- Update systems and software. Staff should operate devices with updated software
- Secure office Wireless network access. IT departments should focus on network hardening where default settings are changed to reduce the risk of attack over the network and via connected devices like printers etc.
4. Security assessments;
Organizations do scale from time to time and their IT infrastructure and digital resources witness a lot of changes over time. Taking the change in the business as a result of the pandemic, organizations are prone to newer and complex risks. To identify security loopholes, mitigate risks, and put precautionary measures in place periodic security assessments like physical security assessments have to be done.
Oftentimes, organizations think they know and understand the gaps in their organizational infrastructure, but if taken note of, another party may be able to pinpoint additional weaknesses. The findings in a report from an external consultant may help validate current concerns and aid requests to have these shortcomings addressed.
5. In-depth network protection; for network protection, an in-depth analysis gives assurance that everything is covered. This includes network security applications like network Access Control (NAC) which is placed to identify rogue devices on the network through detecting new MAC (Media Access Control) addresses.
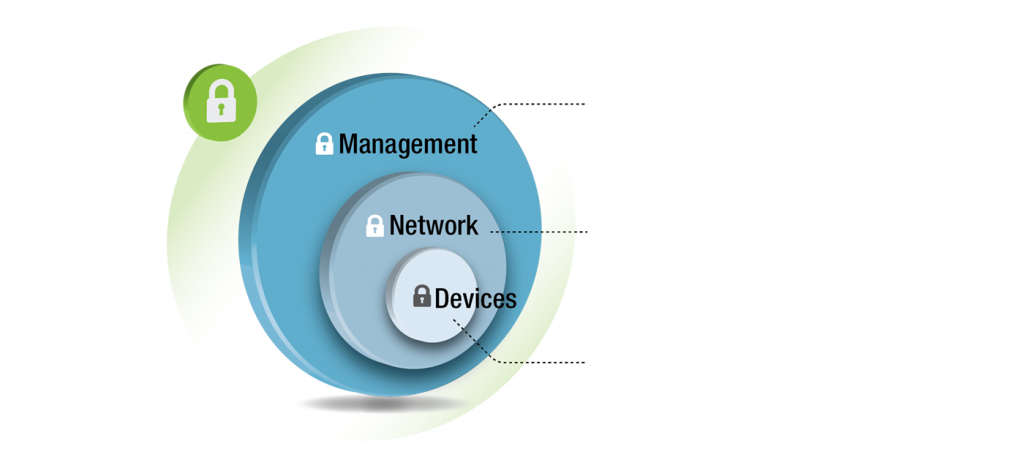
Securing endpoint devices and monitoring network inventory for any new connected devices. Rogue devices such as USB devices are more difficult to catch because they will often masquerade as innocuous devices on the network, Thorough logging of USB devices can help detect these devices. With encryption of devices like hard drives, mobile handsets, information on these devices is safe and an attacker may not be able to recover any of it
Remarks
The winning insight that our CEO aired to organizations was cybersecurity awareness for organizations is key. He had this to say;

“As cyber threats against organizations continue to grow (year after year), so does the need for cybersecurity awareness, vulnerability assessments, real-time threat intelligence tools, incident response planning, and cyber insurance. At the bare minimum, organizations need to undertake effective cybersecurity awareness training programs so that all staff plays their part by recognizing signs of cybersecurity threats and taking recommended action and best practices.”
Visit https://www.summitcl.com/free-webinar-on-cybersecurity-hygiene-to-improve-your-security/ to book free cybersecurity talk to your organization and empower your staff.

