If you access the Internet or use WhatsApp, Email, Skype and any social media app, you are vulnerable to phishing. Derived from the fishing hook, phishing cyber-attack vector tricks victims into clicking on links that appear to come from genuine sources.
In 2019, the phishing attack is projected to be one of the top schemes deployed by cybercriminals. For this reason, most of the sensitizations on the highest forms of cyber-attacks focus on different forms of phishing attacks always launched, especially to the end-user.
How phishing works
Jane (not real name), has a mobile phone with Internet access. She opens a Facebook account and a LinkedIn account. She does not take time to change her social media profile security settings thereby leaving them in default. Thereby allowing any ‘friend’ to view her account profile details. Within a month, Jane gets so many ‘friendship’ requests. Excited about having a huge following, she makes a blanket acceptance. However, one of the ‘friends’, is an enemy. They exploit Jane’s bad security behaviors by obtaining her email address from her account.
In addition, we find most victims submitting their personal information into the different online links in disguise. You have probably received an email in your inbox purporting to be from your bank or University or online service provider. Such an email requests you to activate account or change your password, or update your on-line details for better service delivery. Ignoring the fact that most of these are crackers, who want to make use of that very information to their benefit.
Take the phishing email supposedly from PayPal. We are sure there could be so many victims. Hackers collect so many emails online and they try their luck. Out of 10,000 targets, you could find over 10%, fall victims. That is why at IFIS we focus on user awareness.
This very week, starting 19th August 2019, multiple occasions have been happening on the online community (see Figure 1), where users have been urged to reactivate their accounts, and on submission of the account details, they are received by wrong hands.
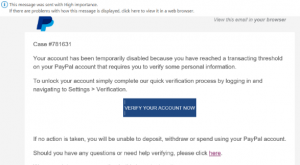
Figure 1 is a classic example of a phishing email.
The email looks as if coming from PayPal. If you have a PayPal account, you could be made to click on the link. The above can happen and formal channels could be used, like emails, however, not every email sent to you is the right email. Some emails might be coming from frauds or cyber-attacks.
When you hover over the link on the “Verify your account now”, it redirects you to a different website, which is not of PayPal as insinuated by the logo on the email. And these have been circulating through-out the weekend.
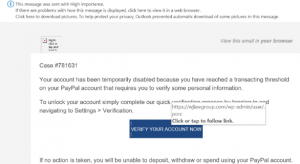
Figure 2: The redirecting email doesn’t forward you to pay pal
Such emails are always sent but before, you send you information, detect the authenticity of the email you are responding to.
HOW IS THIS PHISHING ACT DONE?
Emails can be easily harvested from the internet, and more so on domains which are so open, thus the security of the domain from the server-side should be improved.
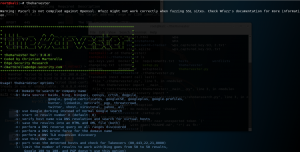
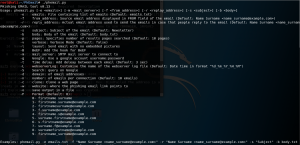
Tools like the harvester, Figure 3, which can be used to capture emails from the domain, thus giving a go to the crackers;
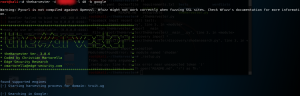
After a fruitful harvest of some emails, the other tool to be used is PhEmail, accessible in Kali Linux to send some fraud emails, via a temporary email (can be attained on the internet).
You need to get sensitized about the risks in cyber-attacks, therefore, more emphasis in our homes, organizations, and different communities should make sure that we get a clear sensitization on cybersecurity. Join us at Summit Consults in partnership with IFIS, on our annual cyber-security awareness and risk management conference, from the 16th – 18th October 2019
For more details and registration procedure, please click here.
Ends.

