Public Wi-Fi is found most popular in public places like airports, coffee shops, malls, restaurants, and hotels. It allows everyone that is short of their mobile data or enthusiastic about wireless connectivity (like it is experienced in most internet users), to access the Internet freely in such places.
These owned networks (Hotspots) are so widespread and common that people frequently connect to them without having second thoughts about them. To users that connect to these networks, it sounds harmless to log on and check their social media accounts or browse some news articles, work mails, opening work portals and platforms, everyday activities that require a login for example checking bank account details among others, could be risky business on public Wi-Fi.
What to worry about when you are not aware?
The problem with public Wi-Fi is that there are a tremendous number of risks that are attached to these networks. While business owners may believe they’re providing a valuable service to their customers, chances are the security on these networks is lax or non-existent.
In regards to the matter in question, it depends on the knowledge and skill of the “WiFi owner” in question and the purpose for creation of the public network.
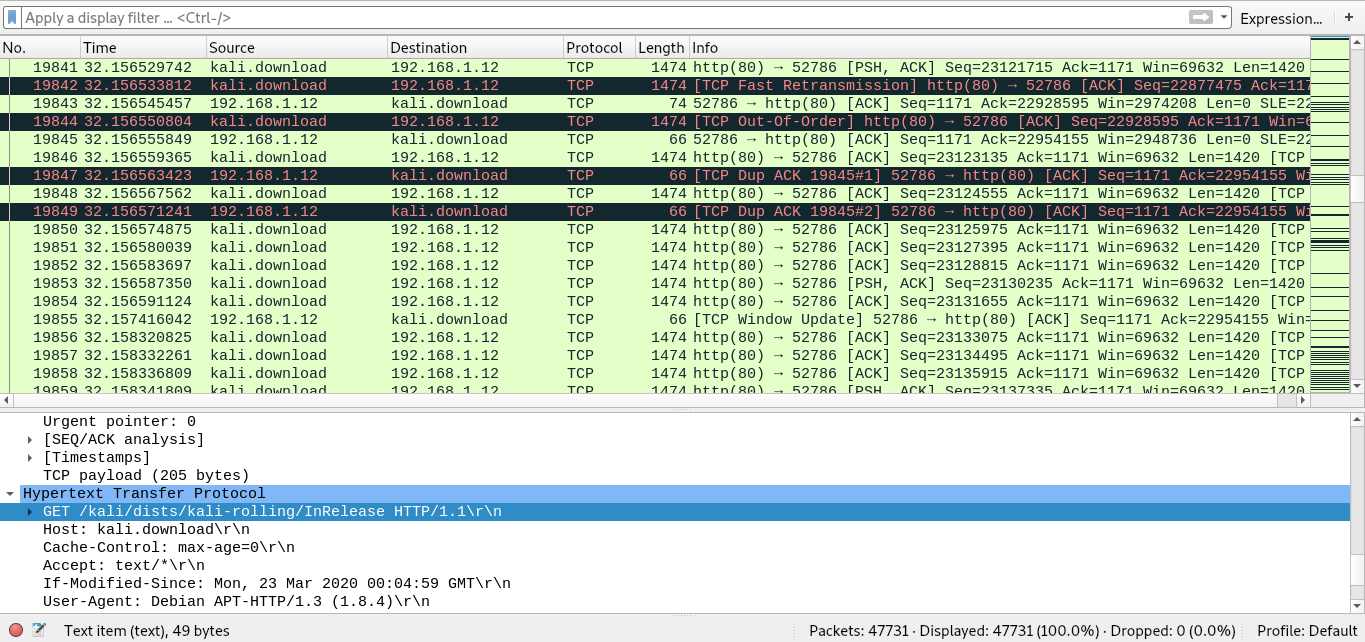
When searching on public network and using an encrypted channel like HTTPS means that yes, the WiFi owner may see that you browsed on HTTPS but unable to see your browsing content. Another issue to note is that when you use a virtual private network (VPN), like Norton Secure VPN, when surfing on your PC, Mac, smartphone or tablet, you will be assured of an anonymized browsing experienced that is not tracked in whatsoever way. That is; A pro could look at router logs or use a packet sniffer tool (like Wireshark) to see that you had traffic to and from Google – but not what you searched for. And if the user browsed on insecure sites that lack SSL and TLS encryption mechanisms and using protocols like telnet, then a pro can get the details of the browsing history and the length of the browsing
The threat that come along with public WiFi
Some of the great mysteries that can never be avoidable on public networks (WiFi) are as below;
a) Man-in-the-Middle attacks
One of the most common unavoidable threats on these networks is called a Man-in-the-Middle (MitM) attack. Essentially, a MitM attack is a form of eavesdropping that mainly is purposed to gather credentials from users that browse on unencrypted sites. When a user is accessing resources on a vulnerable site via an unprotected network, the vulnerabilities can allow an attacker to get in between the user and the vulnerable server data transmissions and “read” them. So, what you thought was private no longer is.
b) Malware distribution
With software vulnerabilities that are run on the devices on the public network, attackers can inject malware onto the devices without the knowledge of the owners. A software vulnerability is a security hole or weakness found in an operating system or software program. Hackers can exploit this weakness by writing code to target a specific vulnerability, and then inject the malware onto the target device.
Caution to employees that are remote working
To all employees that have taken on their responsibility to work remotely, it becomes another issue to note that while in a comfortable working environment, there is a lot of confidential information that is at risk and that needs to be secured and made unavailable to threat actors and confidential data hunters. This is to bring awareness to all that while using public Wi-Fi, always ensure that your activity is shielded by a licensed virtual private network (VPN), like Norton Secure VPN, when surfing on your PC, Mac, smartphone or tablet. However, if you must use public Wi-Fi, follow these tips to protect your information.
What you should not Do:

- Log onto a network that isn’t password protected
- Access websites that hold your sensitive information, such as such as financial or healthcare accounts
- Allow your Wi-Fi to auto-connect to networks
- Log into any account via an app that contains sensitive information. Go to the website instead and verify it uses HTTPS before logging in
- Leave your Wi-Fi or Bluetooth on if you are not using them
What you should do to protect your self:

- Disable file sharing
- Only visit sites using HTTPS
- Log out of accounts when done using them
- Use a VPN, like Norton Secure VPN, to make sure your public Wi-Fi connections are made private
Note: Never and never connect to public networks, always use your network or mobile data but not a network that you are unaware of its security.