Penetration testing is done in different ways, apart from other penetration testing processes, Social Engineering is one of the fundamental techniques and methodologies that is so important, which all organizations should embrace to assess their level of resilience towards information security. As human beings continue to be the weakest link in the security chain, organizations must embrace this kind of testing at both internal and external aspects.
In this article, we are going to assess social engineering penetration testing and why it is important to any organization. we will assess how it can help combat the organization’s resilience towards social engineering attacks and techniques towards the organization’s confidential data.
As there has been noticeably increased dependency on the internet consumption, lurking and to a greater extent over usage of social media, social engineering has been the most noticeable successful attack vector that has worked as the initiator to most data breaches due to successful attempts, this is remarkably noted as a “COMMON PRACTICE”. According to a public view (Wikipedia), it is known as the psychological manipulation of people into performing actions or divulging confidential information. And in that perspective, it is a cybersecurity attack wherein the attacker tricks individuals into revealing confidential information.
What is Social engineering penetration testing?
This is a security assessment that ethical hackers carry out in any organization to assess the resilience of employees towards information security. In the context of information security, ethical hackers or security assessors, simulate social engineering attacks like Social engineers by psychologically manipulating employees to take actions that would end up divulging confidential information. This is purposed to locate weaknesses in the employees (resilience level of the organization) that end up giving away critical information during cyberattacks in case they occur.
By writing this article, we intended to make it as clear as possible of the possible ways or techniques that social engineers (cyberattackers/hackers) deploy when they need to compromise your security by stealing critical information from you as a result of you being a weak link in the organization.
Possible techniques used during social engineering
Many confirmed techniques are deployed and which provide 100% information as intended if launched on individuals with little know-how about such attacks. Some of these techniques that you should know about or heard about or even experienced but had little knowledge of what was happening are as follows;
1. Phishing
 One of the commonest and ever thought of a trick to be used by attackers up-to-date with a 90% result yield is the phishing technique. This is done through email delivery to the victims. It is categorized into targeted emailing (spear phishing) and mass mailing. Attackers create very eye-catching and call to action email messages that deceive the victims into sharing valuable information or clicking malicious/malware-infected files that can infiltrate their systems and install rootkits, keyloggers, spyware into their systems.
One of the commonest and ever thought of a trick to be used by attackers up-to-date with a 90% result yield is the phishing technique. This is done through email delivery to the victims. It is categorized into targeted emailing (spear phishing) and mass mailing. Attackers create very eye-catching and call to action email messages that deceive the victims into sharing valuable information or clicking malicious/malware-infected files that can infiltrate their systems and install rootkits, keyloggers, spyware into their systems.
2. Smishing
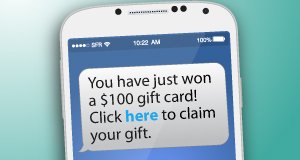
Similar to phishing smishing techniques are done through SMS (text messages). The text messages are written in such a way that they compel the user to disclose sensitive information.
3. Vishing

Just like phishing, this one is done through phone calls instead of emails. In this attack, the attacker calls victims intending to trick them into divulging delicate information amidst the conversation.
4. Impersonation

This is a common technique where attackers attempt to mislead an individual into believing they are legit people or someone they know. Take an example, an attacker could impersonate an employee targeting employees of that organization and aiming at convincing employees to share confidential information like permission to access credentials of the secure network, access to data centers of private company data.
5. Dumpster Diving

With this technique, an attacker does a thorough check-in deleted files, in dumpsters physically, on calendars, emails, sticky notes to get some information that could be noted down.
6. USB Drops/Baiting
 This is where an attacker uses USBs with malicious content, drops them around the workspaces of interest. The USBs consist of software that when plugged into the system can install malicious software or files that can allow the hacker to enter a secure section.
This is where an attacker uses USBs with malicious content, drops them around the workspaces of interest. The USBs consist of software that when plugged into the system can install malicious software or files that can allow the hacker to enter a secure section.
7. Tailgating

The purpose of this technique is to evade physical security measures. Hackers at times use this when there is a need for biometric access into the premise of interest. All that is done is, they will do all they can to enter the premise by tricking the employees that maybe they are carrying luggage and can not provide biometrics or by waiting and following an employee whose biometrics has been scanned to access the premise
Why social engineering penetration testing is important?
Hackers around the globe are knowledgeable about how employees conduct themselves. They know that users have continuously been regarded as the weakest links in a security system as they never observe the security norm or sometimes new employees could be employed and not briefed of the security cultured in place. These impose a risk of social engineers because they are given access to company data and access to network assets as well as credentials of the company assets to be able to operate in the company.
So, it’s of good practice that organizations perform social engineering simulation attacks on employees to attest to the level of security awareness and attack resilience. Only through these attacks by the organization security tam that organizations can know the need in their security posture and to plan and implement a proper IT budget to cater for the network security after assessment. The kind of social engineering tests are done in two ways that’s; within the company and external assessments to assess the risk outside of the company.
Conclusion
Security assessments are mandatory to any organization that handles the client’s data and its privately-owned data, it’s the responsibility of the organization to ensure that its network assets are protected and that all its publicly available data and privately-owned data is safe and accessible only to the authorized persons.
You can never know when your data becomes insecure, you can never know when a data breach will be launched against you, you can never guarantee a better security posture unless if you combine efforts. Always guard your data like you know that hackers are on their way and protect your assets like you expect a breach any minute!

