Cybersecurity analysts can only secure a network when they have good situational awareness of the systems and devices on that network. Nmap, short for “Network Mapper” is an open-source utility for network discovery and security auditing. It is one of the most important tools available for cybersecurity professionals, network engineers, and system administrators to perform useful tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
With dozens of new devices appearing on the networks of large organizations every day, Nmap uses raw IP packets in novel ways to determine the hosts available on the network, the services offered by hosts, and what type of packet filters or firewalls are in use. If too many ports are open, the devices might be vulnerable to attack. Nmap, therefore, empowers you to scan networked devices to determine the services being exposed on the network, verify firewall configurations, and conduct network troubleshooting.
Disclaimer
This article is for educational purposes only. IFIS is not responsible for any illegal activities conducted on any system you do not have permission to analyse. Nmap is a security testing tool and you must be extremely careful with how you use it to avoid running afoul of the law. Remember, attackers use these tools also and if you run a scan without permission, you might appear to be an attacker from someone else’s point of view.
There are different Nmap versions available for Linux, Windows, and Mac operating systems. The basic Nmap tool works at the command line while Zenmap offers the official Nmap Security Scanner GUI. We shall use Scanme.Nmap.Org, a service provided by the Nmap Security Scanner Project to foster the learning of Nmap. Let’s now navigate some of the essential Nmap features.
The Default Nmap Scan
Before we run the basic scan, let us first see how Nmap presents its results. Nmap will provide you with a list of ports that it detected, and then provide state information for each one of those ports. There are four possible states:
- Open ports listening for incoming connection requests and responding to those connections.
- Closed ports that seem to be accessible to the scanner, but with no service responding to connection requests.
- Filtered ports that Nmap attempted to scan, but a firewall interfered with the scan.
- Lastly, unfiltered ports that Nmap was able to access, but for some reason was not able to determine whether the port was open or closed.
With that background, let’s perform a basic scan of the scanme.nmap.org server. We simply type nmap and then the DNS name or IP address of the server, scanme.nmap.org.
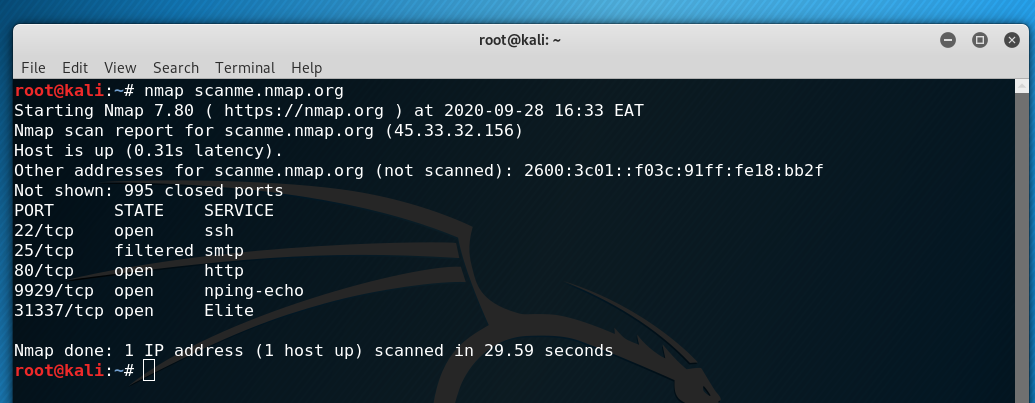
In this default scan, Nmap tracks 1000 ports and we see that 995 of those ports are closed. For each port, there is a port number and protocol, the state, and then the service that Nmap believes is running on that port.
The first result, for instance, shows TCP port 22 that is associated with the Secure Shell (SSH) service. You can also choose to scan a list of systems or an entire network by providing a list of IP addresses and DNS names separated with spaces, a range of IP addresses or subnet mask, or DNS names and IP addresses stored in a file.
Host Discovery
Since there are over 65,000 TCP ports on a given system, port scanning can be a time-consuming task. Nmap uses host discovery techniques to minimize the amount of time that it spends scanning addresses that either are not assigned to a system or don’t have any exposed services. Host discovery attempts to figure out whether an address is active before scanning ports on the system
By default, Nmap performs host discovery sending an ICMP Echo Request to the remote system. If the scanner receives an ICMP Echo Reply, it knows that there is a system at the address and then launches into a port scan. However, many systems don’t answer ICMP Echo Requests. In those cases, Nmap moves to sending connection requests directly to port 80 and 443, two TCP ports that are commonly used for public services. If the scanner receives a reply, then it launches into the port scan.
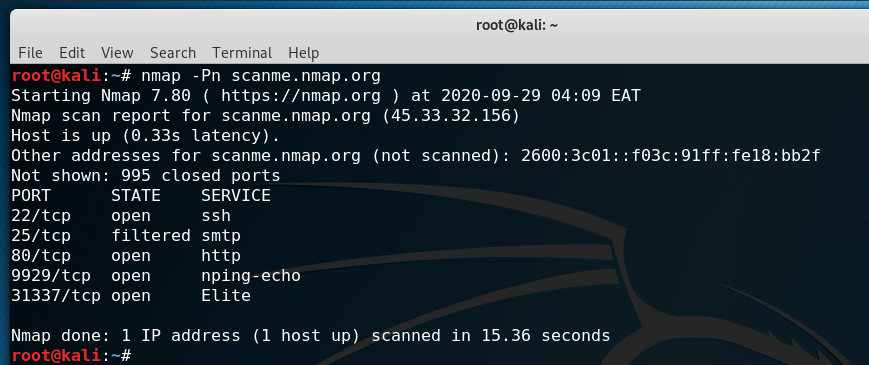
You can customize the way Nmap performs host discovery by adding flags to your Nmap request. The most commonly used flag is the -Pn flag. When you specify this flag, Nmap skips the host discovery process and performs a full scan of the target system.
Port Selection
While Nmap does many things, its most fundamental feature is port scanning. Port selection allows us to customize our Nmap scans by specifying the ports that we would like to scan to meets our objectives. Previously, we’ve been conducting Nmap scans without specifying any ports. This causes Nmap to use its default option, which is scanning the 1000 most commonly used TCP ports.
It’s important to note that there are 65,535 TCP ports on a system. Many of those are probably not used on your network, and scanning each unused port does take some time. If a service is running on any of those ports other than the 1000 most commonly used, a default Nmap scan will miss that port.
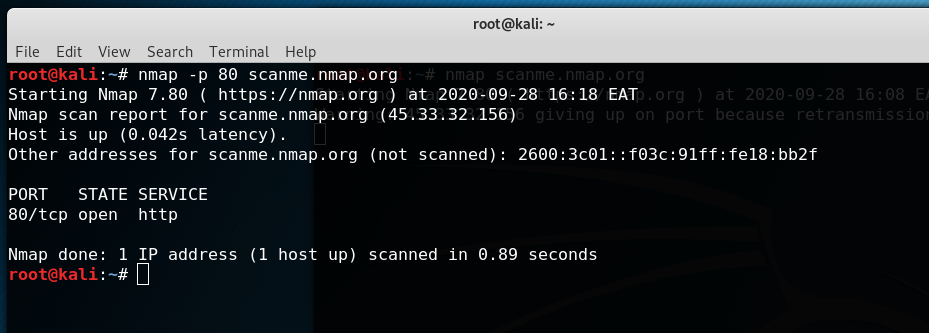
The -p Nmap flag allows us to specify the exact ports by number or by service. We can try scanning the same server only on port 80 to see if it is running an HTTP service.
OS Detection
Fingerprinting of target systems provides more detailed reconnaissance that is useful for determining vulnerabilities and for tailoring effective exploits for those vulnerabilities. Nmap includes a huge database of heuristics for identifying thousands of different systems based on how they respond to a selection of TCP/IP probes. Open TCP and UDP ports are interrogated to ascertain device type and OS details.
We can activate Nmap operating system detection using the -O flag. Let’s determine the operating system of the scanme.nmap.org server.
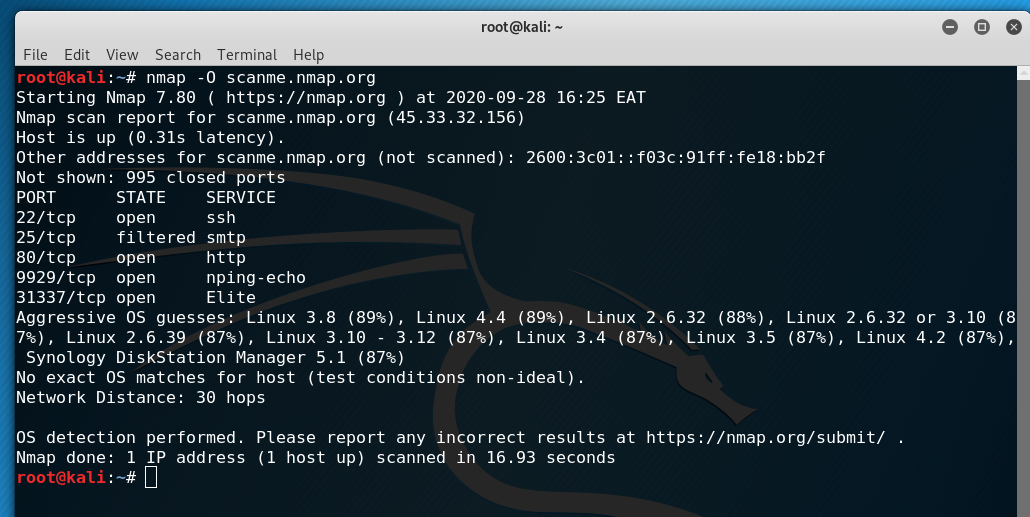
Looking at the results, we see the Nmap has no exact OS matches but provided options of a server running some version of Linux. One of the reasons for this is that operating system detection doesn’t work optimally when run over a long distance, which is 30 hops in this case. Operating system detection, therefore, works better on local networks.
Version Detection
In addition to identifying operating systems on targets, Nmap is also able to deeply analyse the services running on a target system. Nmap gathers information from the service banner and network behaviour and attempts to identify the specific software running on that port as well as its version number. We can activate service version detection using the -sV flag.
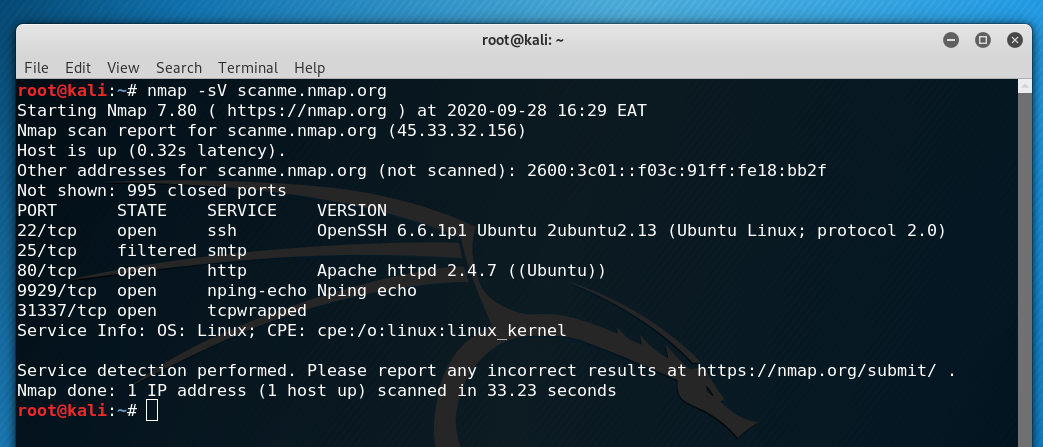
The results above contain some very detailed information. With version detection, Nmap establishes that Scanme.Nmap.Org is using Ubuntu Linux, and offers more information about the services running on the system.
We get to discover that the SSH server is running OpenSSH version 6.6.1 patch 1 and Apache version 2.4.7, which would be very useful if we knew of vulnerabilities in those particular versions.
Nmap Scripting Engine (NSE)
The Nmap Scripting Engine is one of Nmap’s most powerful and flexible features that allows customized testing of the target systems with user-defined or community developed scripts to automate a wide variety of networking tasks ranging from network discovery to more sophisticated version detection, vulnerability detection, backdoor detection, and vulnerability exploitation.
Nmap’s -A flag, for example, activates the Nmap Scripting Engine and turns on several testing options that provide details about the target system and its network location. This flag, together with the T4 aggressive timing template, enables remote operating system detection, activates service and version detection, and requests a traceroute to the target.
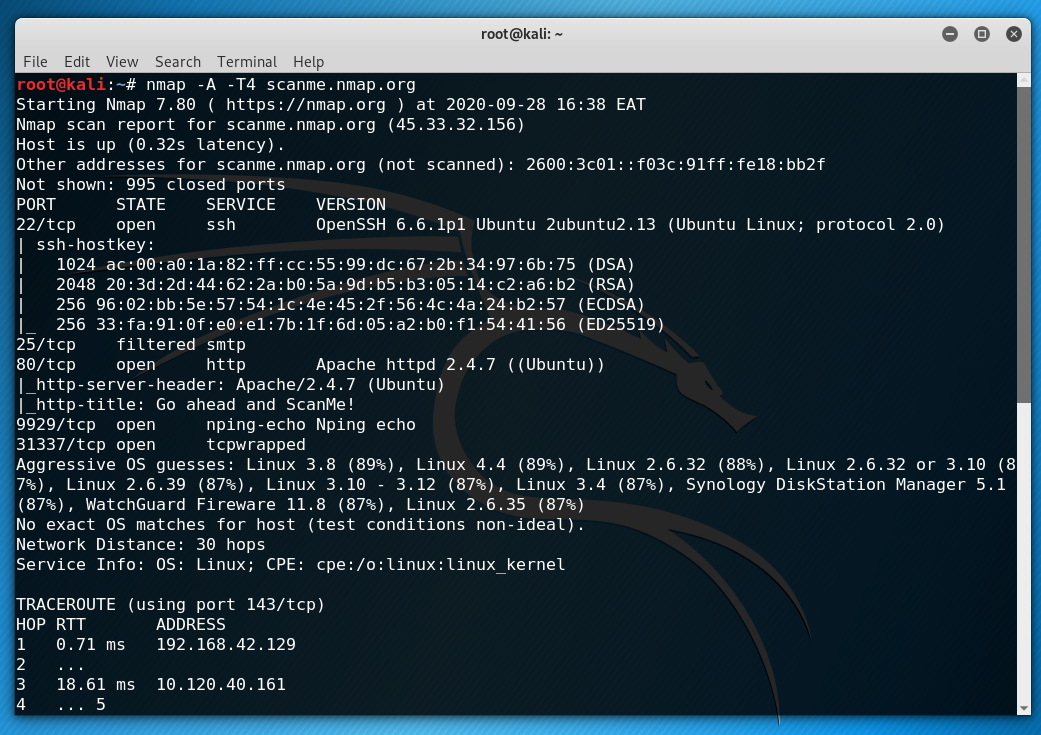
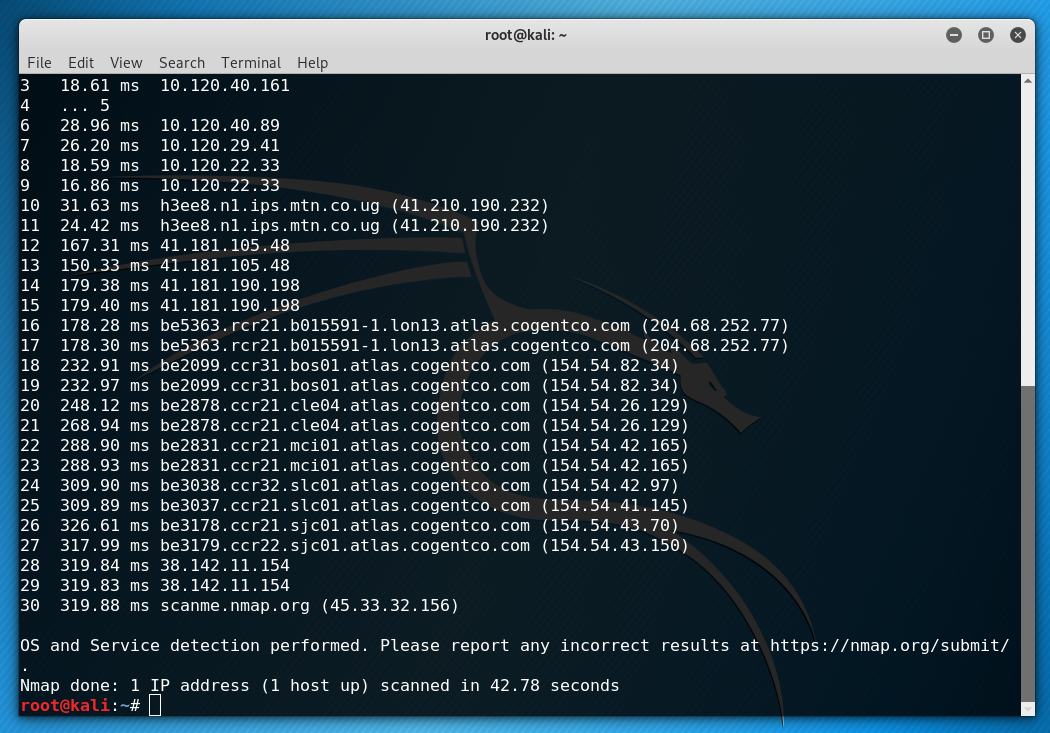
There is much more we can do with Nmap and other network security tools to ensure a robust enterprise network. Get in touch with us as we strive to improve your cybersecurity testing program.

