Course News & Blogs
- All Posts
- Blog
- Career Management
- Computer Security
- Cyber Defence
- Cyber Incidence Response
- Cyber Preparedness
- Cyber Security
- Data Privacy
- Endpoint Security
- Fraud Investigation and Examination
- Fraud Management
- IT Security Audit
- Marketing
- Mobile Security
- Training
- UX/UI Design
- Web Development

Why most frauds are discovered too late Most fraud is not hidden behind complex code or secret accounts. It hides...

The rise of invisible theft It doesn’t start with a gun. It starts with a click. A wrong link. A...

When fraud happens, it is never out of the blue. The signs are always there, ignored, excused, or misread. As...
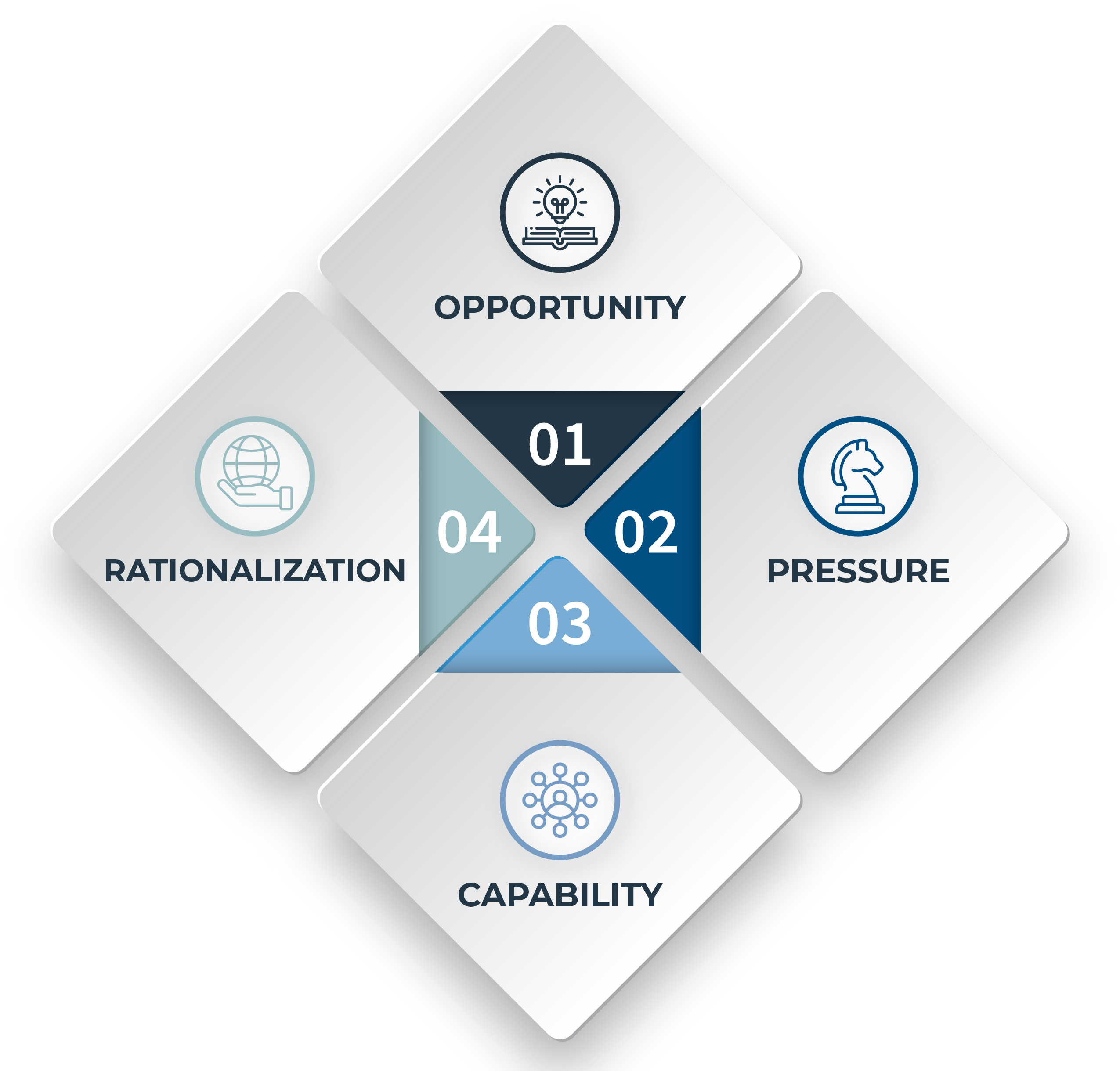
Fraud doesn’t begin with bad people. It begins with pressure. With a quiet “just this once.” With a system that...

Fraud doesn’t knock. It walks right in through your open doors, process gaps, ignored red flags, and blind trust. And...
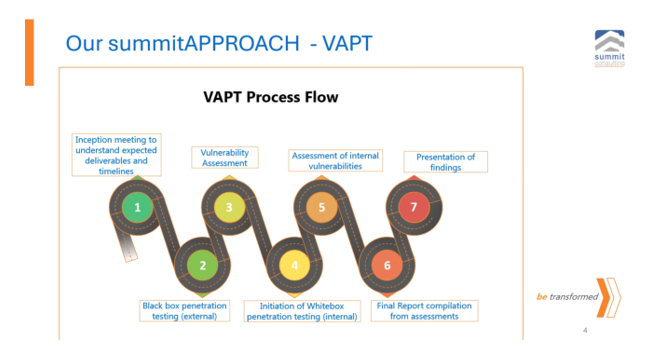
You have a penetration testing process. You have a risk management department. You have an internal audit team. Yet you...

On 11th February 2025, a procurement officer at a prominent government parastatal in Entebbe signed off an “emergency” UGX 360...

Everyone loves to preach about “trust.” It is easy. It feels good. It looks good on glossy company brochures and...

A padlock on a chicken coop means nothing if the fox has the keys. In a recent cybersecurity audit, we...

A monkey tied to a tree still thinks it is free. That is the modern internet user clicking “I Agree”...

The issue is: Time is not money, it is evidence On 26th February 2025, the CEO of a prominent government...

Most people think hackers wear hoodies and speak in code. That’s Hollywood nonsense. Real hackers don’t need to break your...

You don’t need a high-tech vault. You just need to stop being sloppy. Most small businesses still think cybercrime is...

The incident On the morning of 3rd March 2024, a mid-sized logistics company based in Mombasa, Kenya went dark. All...
In fraud investigations, perception is not enough. You need precision. If your report can not stand cross-examination in court or...

When things go wrong internally; fraud, harassment, data leaks, ghost workers, it is not what happened that destroys your organization....
Dear Executive, Fraud does not always knock. Sometimes it wears a staff ID and walks in smiling. It is so...
Dear Leader, We have seen it too often. A fraud case breaks out. Panic. Headlines. Then… silence. Why? Because the...
Although this is a real case drawn from field experience, the names and locations have been altered to protect confidentiality....
Every entrepreneur talks about success. But no one tells you the price tags attached. Before I pivoted to strategy, risk,...
Dear Managers, Let me start with a simple, real-life scenario A mid-sized financial institution I will call “Bank X” approved...
Years ago, I sat across a jittery CEO of a large logistics company in Zambia. His eyes told the story...

Human error has been highlighted as a major contributing element to cybersecurity vulnerabilities for years. It is a long-standing concern...
Due to the ever-growing threat landscape in the digital ecosystem, your business must embrace cybersecurity irrespective of the size of...
In January 2023, we received a phone call from the CEO of a well-known logistics company. His voice carried the...
How Omundo stole money using ATM cards that were not his This case is about a man who tricked the...
Pornography is a silent pandemic. It claims one victim at a time. Thanks to the Internet, the problem is very...

The first thing they stole was time. For nearly two years, a group of insiders siphoned money from the bank,...

The first thing they stole was time. For nearly two years, a group of insiders siphoned money from the bank,...
Smart devices are convenient, but they are also a hacker’s paradise. Your smart TV, speaker, and even refrigerator are potential...
“Your phone is your financial vault. Lose it carelessly, and you’re handing thieves an open door to your money.” Mobile...
“A good con doesn’t need to be clever it just needs a willing victim.” Every few years, a financial institution...

“A good con doesn’t need to be clever it just needs a willing victim.” Every few years, a financial institution...
Mr Strategy’s Memo on fraud risk Have you ever been accused of a crime you never committed? Imagine waking up...
There’s a pervasive myth in boardrooms and IT departments alike: that with enough investment, training, and fancy software, a company...
Every fraud starts as a ‘necessary adjustment.’ Then it becomes a habit. Then it becomes the business model. Carter’s, a...
Every company has its secrets. Undue enrichment is usually part of them. Stories about a top honcho who stole large...

In an era where financial transactions are becoming increasingly complex and digital, fraud has evolved into one of the most...
In the overcrowded world of cybersecurity certifications, everyone is chasing acronyms you know several. They look good on a LinkedIn...
Umoja SACCO, a mid-sized financial cooperative with 15,000 members, faced growing cybersecurity threats as it digitized its services. It needed...
Dear Executive Team, Cybersecurity doesn’t have to mean writing a blank check. The conventional wisdom screams for bloated Security Operations...

In the digital age, the Internet has become an essential part of daily life, offering numerous opportunities for economic growth,...

Who did what, where, when, and how? An investigation must provide answers to each of these questions concerning the issues...

Application monitoring just like overall network monitoring is a vital IT function for corporate organizations. From employee productivity with the...

Human error has been highlighted as a major contributing element to cybersecurity vulnerabilities for years. It is a long-standing concern...

Due to the ever-growing threat landscape in the digital ecosystem, your business must embrace cybersecurity irrespective of the size of...

Protecting company data, sensitive and high priority information, corporate networks, software, company equipment, and personnel is what makes physical security....

Did you know that 99.7% of applications have at least one vulnerability! Findings from Verizon’s 2020 Data Breach Investigations Report...

In this digital generation, the great shift to mobile devices and technology adoption has tremendously changed our mode of interaction....

In the good old days, before COVID19, the easiest way to keep children from online dangers was to not give...
Career skills that work at IFIS
Enhance your career with courses in Cybersecurity, Fraud Risk Management, and Personal Productivity. Gain the skills to protect systems, manage risks, and optimize your performance. Start today to stay ahead in a competitive job market!

- 12 Lessons
- 16 Studenst
Certified Business Intelligence Data Analyst (CBIDA)

- 12 Lessons
- 16 Studenst
CERTIFIED RISK STRATEGY PROFESSIONAL(CRISP)

- 12 Lessons
- 16 Studenst
CERTIFIED FRAUD FORENSIC PROFESSIONAL (CFFP)

- 12 Lessons
- 16 Studenst



