Why segment your network?
Many of today’s enterprise IT environments are linked to multiple vendors and other interconnected devices to optimize business operations. However, the corporate network’s security is crucial to secure business operations from potential intrusions and keep them running at optimal efficiency.
This brings us to the important concept of network segmentation, which is a core building block for achieving a mature cybersecurity profile. A properly segmented network should have each sub-network (subnet) existing in completely different security and IP zones, and only connecting at very limited points, on very limited ports, through clear points of monitoring. Implementation is basically effected through a combination of virtual local area networks (VLANs) and border firewalls connecting at least three different security zones, that is, the Internet, intranet, and demilitarized zone (DMZ network).
Through our penetration tests and IT audit engagements, we find that many of our clients have hundreds of hosts on completely flat networks where all hosts are routable to all other hosts within the network. Whereas this may simplify network administration and accelerate workflows, it comes with a huge cost of a wider internal attack surface allowing the attacker to move laterally across the network to gain access to credentials, critical systems, and corporate data, through privilege escalation and post-exploitation techniques.
Case Study: Retail giant hacked through a third-party vendor
“Nationwide retail giant Target is investigating a data breach potentially involving millions of customer credit and debit card records, multiple reliable sources tell KrebsOnSecurity. The sources said the breach appears to have begun on or around Black Friday 2013 — by far the busiest shopping day of the year,” mentioned security blogger Brian Krebs on December 18, 2013, in his blog post.
The attackers backed their way into Target’s corporate network by compromising a third-party vendor. That happened to be Fazio Mechanical, a refrigeration contractor. A phishing email duped at least one Fazio employee, allowing Citadel, a variant of the Zeus banking trojan, to be installed on Fazio computers. With Citadel in place, the attackers waited until the malware offered what they were looking for — Fazio Mechanical’s login credentials. At the time of the breach, all major versions of enterprise anti-malware detected the Citadel malware whereas the third party had deployed Malwarebytes free edition, which did not offer real-time protection.
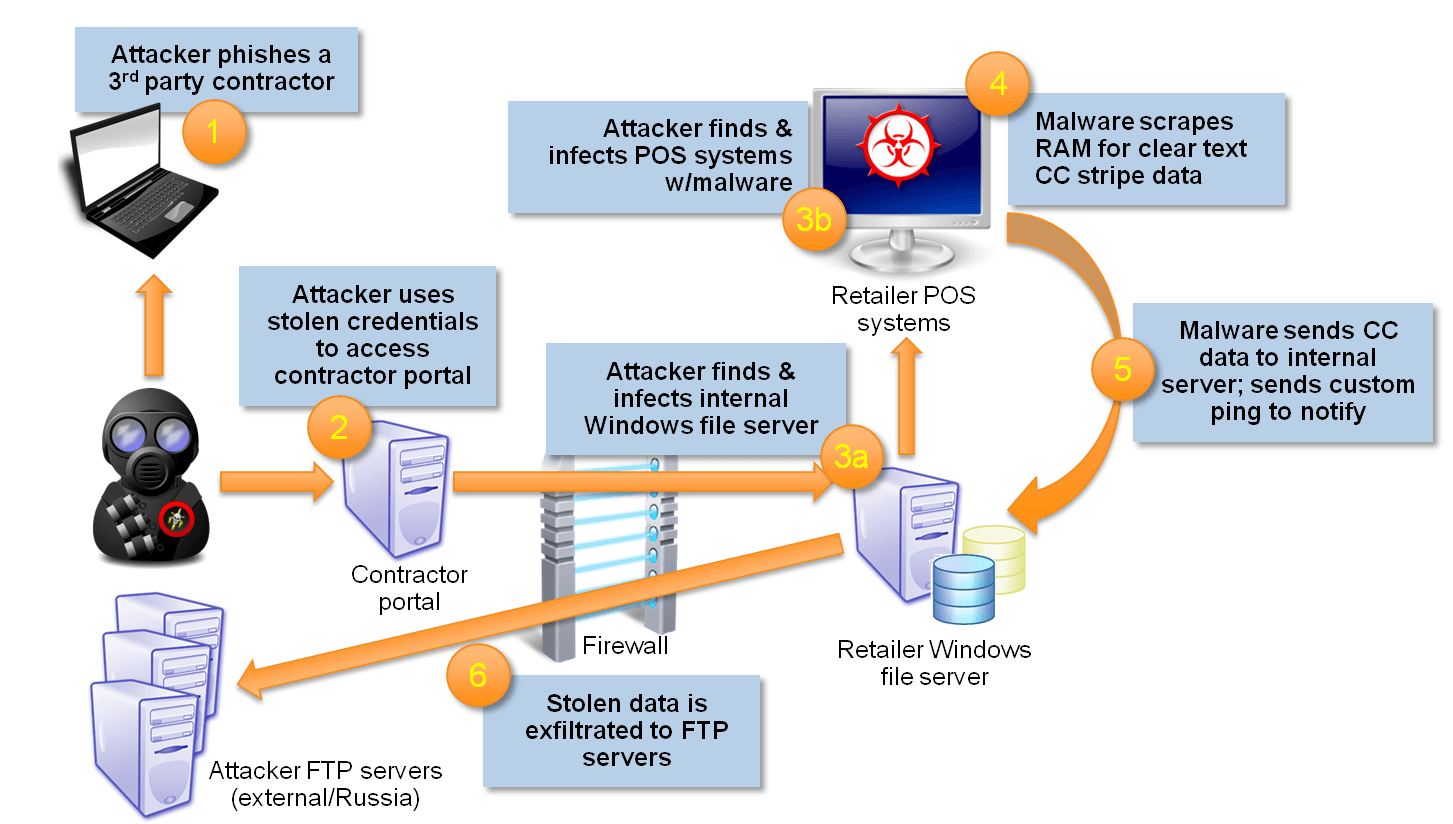
Upon acquiring the vendor’s credentials, Target’s point of sale (POS) systems were infected with a malware code-named Trojan.POSRAM. The “RAM-scraping“malware (malware obtaining unencrypted customer information stored temporarily in the terminals) grabbed credit card information from the memory of POS devices as cards were swiped.
In the aftermath, approximately 40 million credit and debit cards were impacted between 27th November and 15th December 2013 (19 days) in the United States, almost about a sixth of the US population at that time. It is one of the largest credit card breaches in history which resulted in serious damage to the Target brand. In as much as insurance covered 90 million dollars, Target had to spend more than 200 million dollars in breach-related expenses and lawsuits.
Key takeaways from the Target breach
- Ensure that you have appropriate access controls in place to identify, authenticate, and authorize third-party users. In this case, Target either didn’t have an extranet or didn’t implement sufficient protections to limit the access that vendors like Fazio had to internal systems.
- Strong network segmentation would have significantly reduced the damage from the Target breach. Well-designed networks group systems into segments based on security levels such that the attacker is not immediately able to see every server (file shares, SQL servers, web servers, etc.) or workstation connected to the internal network.
- Segmentation enables defenders to detect strange malicious behaviour within their network by getting alerts from hosts attempting to access unauthorized systems. Network activity monitoring could help Target identify regular pings suddenly emitting from POS systems, and also recognize regular but transient Windows shares being created and removed shortly thereafter.
- Proper segmentation, therefore, hardens an organization’s network controls by separating critical networks from the Internet and other less sensitive internal networks.
Is your network safe?






Responses