Did you know that 99.7% of applications have at least one vulnerability!
Findings from Verizon’s 2020 Data Breach Investigations Report show that malicious attackers take advantage of application weaknesses and software vulnerabilities. This is to conduct data breaches against organizations. This is the ever-known most common external attack method.
More cybersecurity statistics from security researchers have it that application vulnerabilities will continue to be the common attack method. Malicious attackers lurk in the digital sphere hunting for either software vulnerabilities or web applications.
This is undoubtedly an eye-opener for you who is concerned about the sensitivity of the information on the applications. And also to you who develops the applications of your organization, right? I have to admit, that as a security practitioner, I’m not at all surprised at that number.
Applications bear low-hanging fruits that attract attackers
According to the Cybersecurity threat landscape survey that we conducted in June-July 2021. We note that the common threats that organizations encounter, software vulnerabilities and web application threats most.
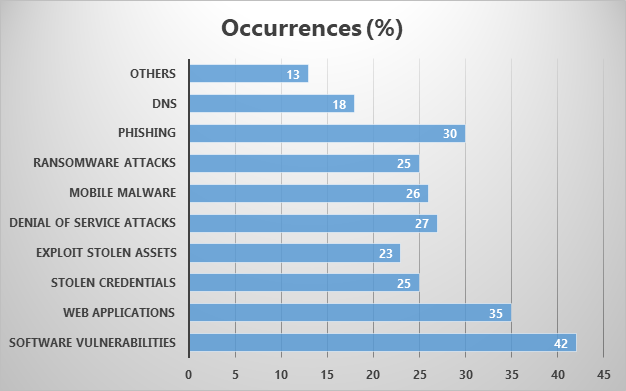
According to the research made by Ponemon Institute, about The Increasing Risk to Enterprise Applications, “They denote that the investment on application security is not commensurate with the risk.” The report denotes a significant gap between the level of application risk and what companies are spending on to protect their applications,” while “the level of risk to other assets like networks is much lower than the investment on network security.”
But most applications are made by big vendors, could they also be malicious?
Amazon, Microsoft and Google have much bigger security budgets than you do. They have hundreds of people all over the world ensuring that their infrastructure is secure. Their teams are constantly reviewing their code, looking for flaws, vulnerabilities and potential exploits. They monitor hacking forums and run attractive bug-bounty programs to remain proactive.
Only a few years ago, kernel errors were prevalent. Now, Microsoft’s and Linux’ teams have nearly eliminated kernel vulnerabilities. For example, according to the CVE database, in 2017 Linux kernel had 169 code execution vulnerabilities, in 2018 only three and 2019 just five.
Are cloud applications safer?

In most of our field security endeavours. We exchange thoughts with many leaders of various organizations about securing the evolving technology. Organizations seemingly compare their infrastructure to the cloud. But when it comes to cloud platforms. The cloud host or providers take as many precautions and invest greatly in securing the cloud. The only defect is the clients on the cloud are duly responsible for the security of their applications in the cloud. This is where the danger lasts.
Very many organizations have developers for their applications and or which outsource their application requirements to external software vendors. In most cases, the developers utilize software architectures and or templates distributed across the public cloud. They use these to develop the applications that organizations use to handle sensitive information.
The pieces of code or templates of applications that developers use for customization into whatever applications that organizations use. Contain their developed pieces from scratch, open-source codes and third-party products, over which developers have no control. So there are so many weaknesses and or threats that come along with these pieces of software. These weaknesses are not addressed which may lead to security compromises.
Attackers are much aware that developers don’t prioritise security aspects in the software development life cycle. Or miss out on certain aspects. This gives them chance to alter existing applications or inject additional code and turn legitimate software into malicious ones. This kind of vulnerability is listed in the “code execution” category, noted as the biggest group in the CVE database.
“Research has it that on average, organizations need more than 50days to patch known vulnerabilities. But on the other hand, hacktivists just need a few minutes to locate these and exploit them to their interests. “
Applications are a potential threat to the security of critical information systems of organizations. How do we protect them?

If there is going to be a secure environment where exiting software applications are at manageable risk. Organizations need to make sure that their application security practices evolve beyond the traditional ways of blocking traffic. They need to understand that investing heavily in network security is not enough.
There is a need to focus the application security in various ways. This will involve investing in application security testing tools during the entire software development lifecycle. The Security scanning tools identify areas of weakness and malicious codes and remediate the likelihood during development. Runtime protection works when applications are in production. It’s important to remember that runtime protection tools provide an extra layer of protection. But these are not an alternative to scanning.
The security scanning tools are not entirely the solution to the problem and their goal is prevention. The tools detect and remediate vulnerabilities in applications before running applications in a production environment.
In most of our security assessments at Summit Consulting Ltd, we have conducted vulnerability assessments on thousands of applications over these years. But what worries, we haven’t encountered a single application that did not have a vulnerability!
Conclusion
If you’ve not done a security audit (VAPT) for your application until now. Get up to speed and conduct one right away. And if you’ve been there before, I’m pretty confident you know the power of regular audits by now.
Ready for your first VAPT? Have questions? Contact +256782610333 or strategy@summitcl.com





