
The war room is an interesting place – you get to see everything in action. The iShield360 cybersecurity center monitors...

The war room is an interesting place – you get to see everything in action. The iShield360 cybersecurity center monitors...

It all starts with a compromise It always begins with a password. In June 2024, a procurement officer at a...

One Wednesday morning in August 2024, the Finance Director of a top-tier insurance company in the region clicked an email...
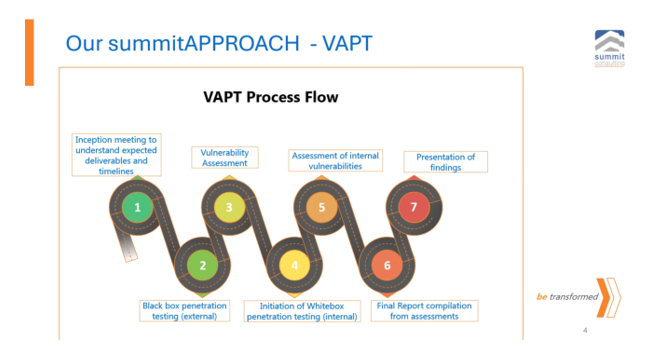
You have a penetration testing process. You have a risk management department. You have an internal audit team. Yet you...

A padlock on a chicken coop means nothing if the fox has the keys. In a recent cybersecurity audit, we...

A monkey tied to a tree still thinks it is free. That is the modern internet user clicking “I Agree”...

Most people think hackers wear hoodies and speak in code. That’s Hollywood nonsense. Real hackers don’t need to break your...

The incident On the morning of 3rd March 2024, a mid-sized logistics company based in Mombasa, Kenya went dark. All...
Although this is a real case drawn from field experience, the names and locations have been altered to protect confidentiality....
Every entrepreneur talks about success. But no one tells you the price tags attached. Before I pivoted to strategy, risk,...

we specialize in bridging the gap between knowledge and application.


© 2025 All rights reserved Institute of Forensics and ICT Security | IFIS is the training arm of Summit Consulting Ltd