
Why most frauds are discovered too late Most fraud is not hidden behind complex code or secret accounts. It hides...

Why most frauds are discovered too late Most fraud is not hidden behind complex code or secret accounts. It hides...

The rise of invisible theft It doesn’t start with a gun. It starts with a click. A wrong link. A...

When fraud happens, it is never out of the blue. The signs are always there, ignored, excused, or misread. As...
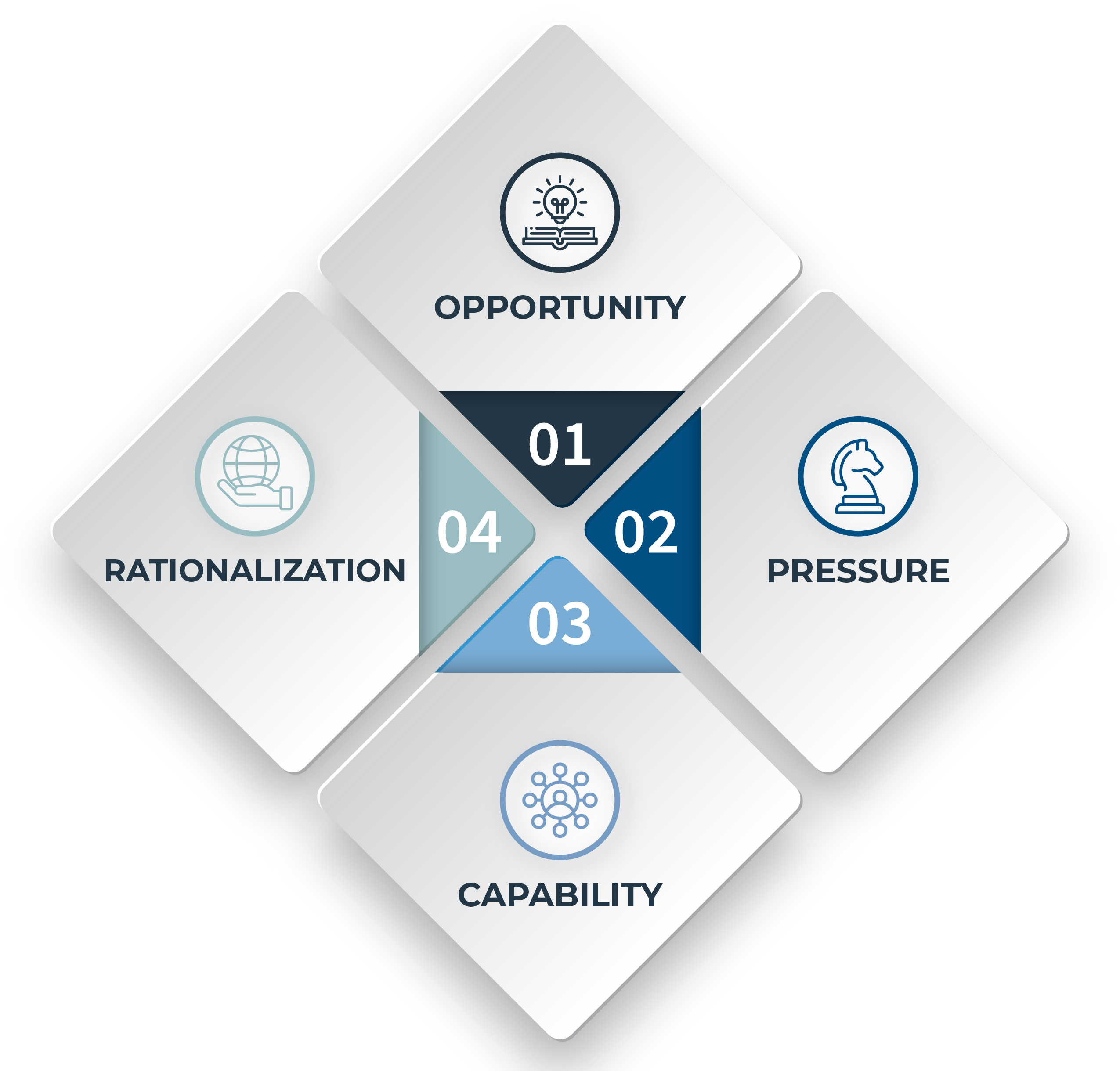
Fraud doesn’t begin with bad people. It begins with pressure. With a quiet “just this once.” With a system that...

Fraud doesn’t knock. It walks right in through your open doors, process gaps, ignored red flags, and blind trust. And...

On 11th February 2025, a procurement officer at a prominent government parastatal in Entebbe signed off an “emergency” UGX 360...

A padlock on a chicken coop means nothing if the fox has the keys. In a recent cybersecurity audit, we...

A monkey tied to a tree still thinks it is free. That is the modern internet user clicking “I Agree”...

The issue is: Time is not money, it is evidence On 26th February 2025, the CEO of a prominent government...

Most people think hackers wear hoodies and speak in code. That’s Hollywood nonsense. Real hackers don’t need to break your...

we specialize in bridging the gap between knowledge and application.


© 2025 All rights reserved Institute of Forensics and ICT Security | IFIS is the training arm of Summit Consulting Ltd