The incident
On the morning of 3rd March 2024, a mid-sized logistics company based in Mombasa, Kenya went dark. All systems dispatch, email, finance froze. A red screen replaced the company’s normal login portal. The message: “Your data is encrypted. Pay $1.5M in Bitcoin within 72 hours or lose it forever.” The firm’s entire fleet coordination collapsed. By day two, port operations flagged the company for delays. By day three, clients began shifting to competitors.
That’s how it starts. Not with fireworks. With one staff member clicking a fake invoice attachment titled “Revised LPO – Urgent”.
You’d think a logistics company would have ironclad cybersecurity. Wrong. Most East African firms treat cybersecurity as an IT matter. But ransomware doesn’t attack systems. It attacks people. And people click.
The IT Manager tried to downplay it. The CEO initially refused to pay. Legal flagged regulatory issues. But the firm couldn’t process a single delivery. By day five, their entire April shipment backlog had been forfeited to rivals. This wasn’t a data loss incident. It was a reputation meltdown.
We were brought in on day six, after one of their clients also our client alerted us to the suspicious blackout. Within hours, we were on ground with our cyber incident response team.

The scheme
i) The attacker used a spear-phishing email with a spoofed supplier domain.
ii) The email contained a malicious macro embedded in a Word document.
iii) Once executed, the ransomware LockBit 3.0 variant propagated via shared folders.
iv) Within 15 minutes, it disabled all backups connected to the network.
v) The attackers used Cobalt Strike to maintain persistence and exfiltrated critical data.
Their vulnerability? Poor email filtering. Shared admin credentials. No offline backups
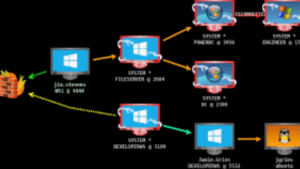
The forensic red flags
Our audit picked up several signs missed by internal IT:
i) A login attempt at 2:43am from an IP in Belarus.
ii) Sudden traffic spikes to *.onion domains (Dark Web).
iii) 28GB exfiltrated to an unknown external server via HTTPS.
iv) Disabled antivirus via Group Policy on three machines simultaneously.
v) No endpoint detection or MFA on admin accounts.
The cost
Total losses tallied UGX 9.3 billion. That’s just direct losses revenue lost, clients cancelled, systems rebuilt. It does not include brand damage or the CEO’s resignation that followed. When you measure in lost trust, the number is far higher.
f) Case in point
In 2010, a young woman from Ntinda walked into our office. She had clicked a link while applying for a bursary online. Her laptop got locked with a pop-up asking for $300. She ignored it. But it didn’t stop there. The ransomware spread to the school’s shared systems, wiping parent records. The school, unaware of the source, fired the bursar. That woman never told anyone it started with her. But her face told the whole story.
g) What this means for you
You don’t need millions to be a target. Just internet. And an employee who’s in a hurry.
Cyber-crime is a silent war. No alarms. No patrols. Just a single click. And silence.
By the time you know you’ve been hacked, it’s too late.
Be proactive. Review your systems. Or wait for the ransom note.





