Take caution, prevent hackers’ access to your bank accounts

In the realm of this fourth industrial revolution, the security of our accounts starts with the creators/owners of the accounts. In many data breaches that have ever happened, it has been noticed that these start with weakly protected accounts and the laxity of account owners in addition to other causes.
One other case to be noted is companies (Banks and other financial institutions) have not taken into account policies governing vendors and software utilization from their vendors. Some may have these policies in place but are not Board approved. These outcomes of not involving the Board may affect the Organization’s reputation. Board is likely to ensure that clients’ confidential data remains confidential and not disclosed to the outside world.

The worst-case scenario happens when the vendors distribute harmful software that comes along with backdoors (software codes that give hackers access to secure systems) and other malware like spyware (that inspect the entire system and reports daily activities and operations of the system where it is installed) and keyloggers (that send timely updates in form of keystrokes that are invoked on the system or screenshots of current sessions on the system).
The organization’s goal is to ensure that its client’s needs are fulfilled and to bring services as closely as possible to its clients. This has greatly brought about the need for outsourcing and the utilization of third-party software from vendors. It is through the flaws in the software that hackers establish their way to secure systems. Once hackers access the system through the backdoors, their restriction to the system and access to anything including confidential data (that they hunt for anyway) is uncontrolled.
Scope

Now as an account owner in a bank or social media forum, you need to assume that your password isn’t strong enough. You might as well believe that someone, somewhere, is working around the clock to break into your accounts and steal your money, social security number, your identity and anything else you have. Because it’s essentially true.
Maybe you’ve taken precautions. You use security software. You have set up your router’s security so cybercriminals cannot access every device on your network, get your passwords or compromise your systems and use them as malicious computers (botnet) in their DDoS attacks at any one time.
After you do that, you’re far from done and it will cause a sense of security around you since you will be aware of what cybercriminals are capable of. Hackers are smart and always on the move.
As an organization, individual, you would not love to come out of Quarantine and find what you left locked to be wide open without the information that you locked, or find computers inaccessible, or accounts so empty of money and with annoying notifications below on your desktop.
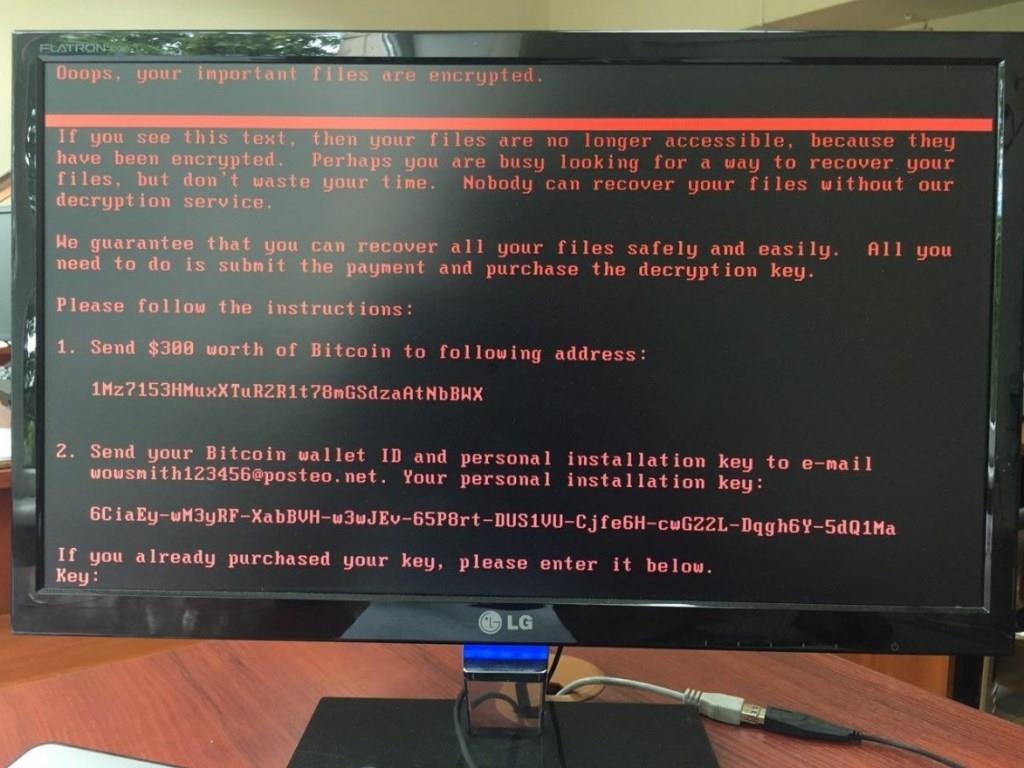
The following will add a layer of savviness to you and to the level of your personal or organizational network asset security, your nest egg and all your considered confidential future in order to add a layer of resilience to the available security measures.
a) Password management

Up to this date, the laxity of password management to many account owners is still poor. It may seem obvious that you need a strong password to keep hackers from accessing your private information and financial reports. Millions of people are still using insecure passwords like 12345678, Password and first names like peter, Paul, etc. It is also noticed that the same password is used for multiple accounts.
How to harden your password;
- Should contain a random collection of letters (uppercase and lowercase), numbers and symbols
- Should Be eight characters or longer
- It should be unique for every account.
b) Make it harder for hackers to crack the code
Hackers can quickly figure out your password, but they can’t figure out the secret, one-time code that your bank texts to you. Two-factor authentication (2FA) is a powerful security method because hackers would have to physically steal your phone, enter the correct password, and then enter that secret code.
In the wake of large-scale hacks, most major accounts offer two-factor authentication, from social media to banks.
c) Keep track of your money

Most of us have at least one bank account (and often more) plus credit accounts, PayPal and other depositories for our money. These can be hard to keep track of, especially when you have additional investments and personal savings goals.
It’s easier to keep track of your business finances if all these accounts are aggregated in one place, right in front of your eyes.
d) Know your credit score

Your credit score will tell you a lot about hackers. If you see anything suspicious on them, like credit card accounts that you didn’t open, you can alert whichever credit bureau is reporting it, whether it’s Experian, Equifax or TransUnion.
Of course, it’s easier than ever to check your credit report. You can check free sites like the Discover credit card site, which says, “You don’t have to be our customer, and there’s no ding to your credit.”
The important thing is to check your credit reports. You should start with the three credit bureaus, each of which gives you one free credit report every year.
e) Freeze your credit

You may have heard financial advisers telling people to freeze their credit. But you may not know why they’re suggesting that.
Here’s a simple overview. Hackers will have a tough time accessing your personal information if you’ve asked the credit bureaus to freeze your credit . This makes your credit inaccessible even to you the owner, unless you ask them to unfreeze it.






Responses