The first thing Stella noticed was the silence. It wasn’t the usual kind, the quiet hum of people settling into routine, typing away, phones buzzing, printers hissing. No. This was different. It was the kind of silence that crawled up your neck and whispered, “Keep quiet. This is not your battle.” But Stella had seen it. Clear as day. A junior procurement officer had entered the records room and walked out with three LPO books under his shirt. She saw him tuck them into his gym bag. She told herself it was none of her business. Until the fake supplier invoices started appearing. Names she’d never heard of. Firms no one had met. Payments made within hours of submission. And one morning, as she passed the corridor leading to the Finance Manager’s office, she overheard it: “Just delete the last page. He’s already been paid.” Her stomach turned. The tipping point Stella wasn’t new. She’d been at the NGO for six years. She knew things happened. But this was different. This wasn’t corner-cutting. It was theft. Systematic. And somehow, no one else was saying a word. That evening, she stared at her laptop. Her cursor hovered over the whistleblower email address listed in the induction policy, an email no one had ever used. She thought of her kids. Her job. Her reputation. But then she thought of the health centres that never got the medicine. The boreholes that never got repaired. The communities that never stood a chance. She clicked Send. What happened next Within 48 hours, the internal audit team contacted her using a secure channel. They brought in external investigators, our Summit Forensics team. Quietly. Discreetly. We set up a virtual mirror of the payment system. Traced the flows. Flagged the ghost vendors. We followed the money. Each fictitious invoice led to a shell account. Those accounts traced back to three staff members. Including the Finance Manager Stella had overheard. The total fraud? UGX 492 million. Why her courage mattered Stella’s act didn’t just save money. It saved the organisation. Donors were on the verge of blacklisting it. The internal rot was already raising red flags during quarterly reviews. But the moment someone spoke, the chain broke. We helped the organisation set up a real whistleblower program. Not just an email on paper. We trained staff. Created safe reporting lines. Quarterly fraud awareness sessions became mandatory. Every new hire had to sign a culture charter. The culture shift Today, that same office has a phrase painted on its wall in big bold blue: “If you see something, say something. Silence is complicity.” And beneath it, in smaller font: “Because Stella did, we still exist.” Fraud is never a one-man job. It thrives in shadows. In laughter-filled meetings where no one asks real questions. In management teams that value loyalty over integrity. But it only takes one voice to stop it. If you lead an organisation, don’t just train your people to detect fraud. Train them to report it. Build systems that protect the truth-tellers. Honour the ones who speak up. Because fraud doesn’t destroy institutions. Silence does. IFIS Team.
Spot it before it spreads: How to build a fraud-resistant culture
Fraud is not an event. It’s a cultural failure. Fraud doesn’t begin in the finance department. It begins in silence. In excuses. In the unspoken code: “That’s how we do things here.” By the time the money is gone, the rot has already eaten through policy, values, and leadership integrity. In Uganda alone, over 10% of the annual budget is lost annually to internal fraud — most of it preventable. Take the case of the water-for-kickbacks scandal In June 2024, a whistleblower at a government water project in northern Uganda triggered a chain of revelations. What started as “missing pipes” ended with five staff suspended and UGX 1.2 billion unaccounted for. At the heart? A toxic culture. Supervisors approved ghost deliveries. Procurement teams handpicked contractors in exchange for kickbacks. Finance looked away because “everyone was eating.” The anatomy of silence a) Fear of retaliation (i) New staff noticed the fraud but kept quiet, afraid to lose their contracts. (ii) One who tried to speak up was threatened with transfer to a remote post. b) Normalization of deviance (i) Fake site visits were signed off as routine. (ii) Audit logs were deleted. No one questioned the missing documentation. c) Weak leadership tone (i) The project manager never took leave — a classic red flag. (ii) His replacement later confessed they “inherited a system they couldn’t clean up.” What we found in our investigation When we conducted a culture audit using our fraud vulnerability heatmap, the results were chilling. Over 78% of staff said they believed fraud would not be punished if “the person is well connected.” Even more worrying, 62% admitted they would not report fraud if it involved their supervisor. How to disinfect your culture a) Start with leadership discipline (i) If your boss fears leave audits, they are the fraud risk. (ii) Rotate duties. No single point of failure. b) Empower the internal audit (i) Train them in digital forensics. Not just policy checking. (ii) Let them report directly to the Board, not management. c) Reward whistleblowers (i) Pay for tips. It works. (ii) Anonymity is not enough. Protect careers. d) Declare a fraud-free quarter and mean it (i) Tie incentives to ethical performance. (ii) Use data. Track red flags. A fraud-resistant culture isn’t about speeches. It’s about systems. Stop tolerating the small thefts. Because what you permit, you promote. And what you promote becomes the new normal.
Catch me if you can: Tools every investigator needs today
The age of smart thieves and dumb systems We are no longer chasing thugs in balaclavas or masks. Today’s fraudsters wear suits, manage bank accounts, and approve their payments. They don’t steal at night. They steal during working hours using the company Wi-Fi. The problem? Many internal investigators are still using pens and notepads while the criminals are using AI, burner phones, mobile money layering, and VPNs. It’s like bringing a hoe to a drone war. This is your forensic toolbox update. Catch Me If You Can is not just a taunt, it’s a test. And you better have the tools to pass it. The new battleground, from files to firewalls The fraudster’s playground has shifted. Yesterday, it was forged cheques. Today, it’s fake domain emails, insider ERP manipulation, and mobile money micro-thefts. The battlefield is digital. Your tools must be too. At Summit Consulting Ltd, we equip our investigators with tools not just for documentation, but for digital confrontation. Let me walk you through the must-haves. The investigative arsenal. Tools that give you an unfair advantage a) Device imaging kit (i) Clone laptops and mobile phones without alerting the suspect. (ii) Tools like FTK Imager, Autopsy, or Cellebrite UFED let you extract deleted emails, WhatsApp chats, browser histories, even from wiped phones. b) Data analytics software (i) Excel is for accountants. You need IDEA, R2, ACL Analytics, or Power BI to crunch suspicious payment patterns, round-figure transactions, and vendor duplications. (ii) Load the full GL and run anomaly tests. One of our audits revealed a ghost vendor created by reversing and reissuing an invoice with only the last digit changed. c) Metadata extractors (i) A document’s fingerprint is in its metadata. Tools like ExifTool or DocParser tell you when a file was created, modified, or copied. (ii) We once caught a “backdated” supplier contract that was created five days after the payment. d) Open Source Intelligence (OSINT) (i) Fraudsters leave digital footprints on Facebook, LinkedIn, and Twitter. Use Maltego, Recon-ng, or even basic Google dorking to link suspects to unregistered businesses, side gigs, or secret relationships. (ii) We busted a procurement cartel by linking three supplier companies to one wedding photo on Instagram. e) Mobile money forensic tracker (i) Investigators must know how to trace cash through MTN MoMo and Airtel Money APIs. (ii) Use IMEI and transaction logs to track layered transfers. One fraud we investigated involved UGX 10 million being split into 100 transactions of UGX 100,000 moved across agents and cashed out at fuel stations. Essential non-digital tools: old school still rules Fraud is personal. You still need tools that give you psychological and operational dominance. a) Voice recorder and bodycam (i) Always record interviews (discreetly, if your jurisdiction allows. In Uganda, this is not allowed unless you are a law enforcement officer with appropriate legal mandate). Liars forget their lies. Devices like the Spy Pen Recorder or hidden body cams are lifesavers. b) Chain of custody logbook (i) Evidence without custody is garbage. Every device, document, or digital copy must be logged with who accessed it, when, and for what purpose. c) Investigator’s field notebook (i) This is your Bible. Document every observation. Handwriting analysis, mood changes, and security patterns. One scribbled sentence can unlock a case. d) Evidence bag kit (i) Proper tamper-proof bags, labels, gloves, and evidence seals prevent contamination and maintain integrity. Psychological warfare: tools that break suspects A good investigator doesn’t just collect evidence. They extract the truth. That requires psychology. a) DISC profiling and micro-expression training (i) Learn to read people, blinking, fidgeting, and tone changes. We use DISC tools to profile personalities and tailor our interview style. (ii) A Dominant suspect will push back. A Conscientious one will over-explain. Use their psychology against them. b) Statement analysis software (i) Tools like SCAN (Scientific Content Analysis) flag linguistic shifts, e.g., moving from “I” to “we” when describing responsibility. (ii) In one case, a suspect shifted from “I paid” to “we paid” mid-interview. That’s how we knew he had a partner. 6) Investigation management tools: Organize or die You’re not Sherlock Holmes. You can’t keep everything in your head. Use digital case management tools. a) CaseHQ or CaseGuard (i) These platforms let you manage files, link evidence, and tag suspects. (ii) You create timelines, map networks, and log interview summaries, all in one place. b) Digital chain of custody systems (i) These log every file, image, or device collected. No more guesswork in court. (ii) Timestamped, encrypted, tamper-proof. The Summit edge tools we use to blow cases wide open At Summit Consulting Ltd, our investigators use a unique triangulation framework: Follow the money. Follow the behavior. Follow the device. Let me show you a real case. A client had UGX 320 million vanish from petty cash over 14 months. No one noticed. We used: (i) Mobile money forensic analysis to trace staggered withdrawals. (ii) Vendor network mapping to link five “independent” suppliers to the same PO Box. (iii) Device imaging to recover an Excel file on the suspect’s desktop titled “Plan B Payroll”, a list of kickbacks by name and amount. All this from just three tools. Case closed. Two arrests. Funds recovered. Bonus tool: the fraud mindset This cannot be bought. It must be cultivated. The best investigators I’ve trained have one thing in common: they assume guilt and prove innocence. Not the other way around. They know that silence is a symptom, not a conclusion. They read between transactions, not just the transactions. Fraud isn’t about the crime. It’s about the gap between what should have happened and what did. You can’t fight fraud with hope Hope is not an audit strategy. Faith is not an investigative tool. If your toolkit is older than your suspects’ Instagram filters, you’ve already lost. Fraudsters evolve. So must you. Equip your team with the full Fraud 360 toolkit. Invest in forensic tools, not just policy reviews. Train for behavioral detection, not just paper verification. If you don’t, you’ll spend more time writing
Fraud 360: The Complete Circle of Deceit and Detection
Why most frauds are discovered too late Most fraud is not hidden behind complex code or secret accounts. It hides in plain sight inside expense claims, stock records, procurement paperwork, and a wink across the finance desk. The problem is not a lack of policies. It’s a lack of enforcement. Fraud is not a crime of intellect. It is a crime of opportunity, fueled by broken systems, blind trust, and boardroom denial. Welcome to Fraud 360, the complete circle of deceit and detection. In this exposé, I walk you through the anatomy of fraud: how it starts, grows, festers, and finally explodes. Then I show you how to detect and destroy it before it destroys your institution. This is not theory. It’s a lived experience. It’s the fieldwork of Summit Consulting Ltd and our forensic teams across Uganda and East Africa. The seed of a fraud opportunity meets rationalization Fraud does not begin with theft. It begins with entitlement. It starts when the Procurement Officer sees the CEO’s relative awarded a contract without due process. It festers when the IT officer is told to “just pay the vendor; the boss knows them.” It flourishes when internal auditors raise flags and are ignored or worse, transferred. In nearly every fraud we’ve investigated: a) An opportunity existed due to weak internal controls. b) Rationalization followed: “I’m underpaid,” “Everyone is doing it,” “I’ll pay it back.” c) Pressure drove the act: loans, side hustles, or family demands. This is the fraud triangle in motion. But to truly understand fraud, we go beyond triangles, to diamonds and more. We study cycles. The Circle of Deceit: How Fraud Evolves Fraud is not a single event. It is a cycle, a self-reinforcing system of cover-ups and complicity. Here is how the full Fraud 360 circle plays out: a) The setup phase (i) A staff member notices a loophole: double payment systems, poor segregation of duties, or an outdated approval hierarchy. (ii) They test the system for small over-invoicing, delayed entries, and ghost workers. No one notices, and they grow bolder. (iii) They recruit allies, finance staff, suppliers, or internal auditors who are naive, lazy, or compromised. b) The harvest phase (i) Funds begin to move, often through mobile money, disguised fuel payments, petty cash, or inflated per diem. (ii) The scheme becomes organized: suppliers get kickbacks, reconciliations are doctored, and audit trails vanish. (iii) Cover-ups are done by reversing transactions, misclassifying expenses, or forging documentation. c) The tipping point (i) Someone notices. A new auditor. A new boss. Or a whistleblower. (ii) A supplier complains of non-payment for a job they never did. (iii) Cashflows don’t add up, yet there’s no visible loss. The fraud has matured. The Circle of Detection: How Summit Consulting cracks it Fraud leaves fingerprints. The key is knowing where to look. At Summit Consulting Ltd, our forensic audits follow a 6-point detection wheel a) Lifestyle audits We ask: Does the clerk’s lifestyle match their salary? If someone earning UGX 2 million per month is building a UGX 300 million flat in Buwate, we ask questions. b) Data analytics We use Benford’s Law, duplicate testing, and vendor trend analysis to identify suspicious patterns. A vendor winning 80% of contracts? A manager approving their own requisitions? The system tells the truth. c) Digital forensics We extract deleted emails, chat logs, and WhatsApp messages. We trace Momo codes, verify IPs, and retrieve audit trails from ERP systems. The digital trail never lies. d) Control walk-throughs We re-enact transactions literally. We sit in your office and request a payment, just to see who approves, who checks, and who looks away. Fraud thrives where processes are assumed, not followed. e) Key informant interviews We speak to everyone, security guards, tea ladies, and junior staff. Most of the time, they know what’s going on. They just haven’t been asked. f) Surprise verifications We visit warehouses, supplier addresses, and even staff residences. You’d be shocked how many companies pay “service providers” operating from a boda stage. Case in point, the UGX 1.2 billion ghost consultancy scandal In 2023, an agency in Central Uganda hired Summit Consulting Ltd to investigate “invisible expenses” in its ICT budget. The case was textbook. A payment of UGX 230 million was made for a “network diagnostic assessment.” There was no report, no TOR, no contract. Just a requisition and approval. When we traced the account, we found: (i) The supplier had been incorporated 5 months prior by Suspect 1, a junior IT officer’s cousin. (ii) The payment was split into 3 chunks to bypass approval thresholds. (iii) The funds were withdrawn via ATM and mobile money within 48 hours. (iv) Part of it was used to pay for Suspect 2’s wedding a procurement assistant. The clincher? The network diagnostics allegedly “performed” had been copied word-for-word from a free online template. We dug deeper. Three other such consultancies. Total loss: UGX 1.2 billion. All siphoned through a small circle of insiders, aided by silence from those who knew but chose not to speak. Red flags missed by the internal auditor The internal auditor did submit a quarterly report, but it was cosmetic. Why? a) They were using Excel sheets to reconcile transactions from a complex ERP. b) They lacked forensic training and didn’t review mobile money logs. c) Their reports were “reviewed” by the same department heads involved in the fraud. This is the tragedy of most audits: process-focused, not outcome-driven. They check boxes, not behavior. They verify documents, not facts. How internal controls were bypassed The system had policies. But policies are useless if people ignore them. Here’s how the suspects beat the system: a) No segregation of duties: The same officer initiated, approved, and verified payments. b) No due diligence on suppliers: The supplier vetting form was a mere formality. No background check was done. c) Poor documentation: Invoices were paid without delivery notes, signed contracts, or inspection reports. d) Mobile money misuse: Over UGX 400 million was paid via mobile
From clicks to cons protecting yourself from online fraud
The rise of invisible theft It doesn’t start with a gun. It starts with a click. A wrong link. A fake email. A too-good-to-be-true job offer. Online fraud is no longer the exception, it’s the rule. And in Uganda, cases reported to the CID’s Cybercrime Division have quadrupled in the last two years. From Kampala to Kabale, cybercriminals are no longer hiding in the shadows. They’re hiding in your inbox. The con in convenience We investigated a recent case in Mbarara involving a school bursar who lost UGX 38 million to a fake supplier portal. The fraud started with a well-crafted email mimicking the Ministry of Education’s supplier payment platform. Everything looked authentic: logos, language, and layout. All it took was one click. Once she logged in, the fake site harvested her credentials. Within two hours, the fraudsters had logged into the real platform, changed the payment details of three contractors, and diverted the funds to mobile money accounts registered under fake national IDs. How the red flags were spotted It wasn’t the police who spotted it. It was the school’s internal auditor. During routine review, he noticed discrepancies in contractor payment confirmations; payment vouchers existed, but no contractor acknowledged receipt. He called one of them directly. That call saved the school millions more. He froze all pending transfers and initiated a forensic review. When our team from Summit Consulting was brought in, we traced the IP addresses to a rented office space in Kikuubo where a cybercrime ring was using VPNs and rented laptops to coordinate the attacks. These weren’t just unemployed youths; two of them were IT interns from a local university. The money trail The UGX 38 million was broken down and split into 19 different mobile money accounts, each capped below UGX 2 million to avoid triggering suspicious transaction alerts. The withdrawals happened across three districts within hours. This was not amateur fraud. This was industrialized deception. What you must do now If you’re a CEO, audit head, or accountant, stop thinking cybercrime is an IT problem. It’s a leadership problem. It’s a culture problem. And it’s a systems problem. You must invest in continuous fraud risk assessments, mandatory staff leave, dual approvals, and penetration testing. Do not wait for URA or NITA to tell you. Act. Because online fraud doesn’t just steal your money. It erodes trust. And when trust goes, your business dies next.
Fraud alert! 7 red flags every employee should watch out for
When fraud happens, it is never out of the blue. The signs are always there, ignored, excused, or misread. As an internal investigator and strategist, I have seen organizations lose billions simply because no one asked the obvious question. Let me break it down. Fraud does not start with fake invoices or missing cash. It starts with silence. With people minding their own business while corruption blossoms in plain sight. Below are the telltale signs to note. 1) Living beyond means (i) A junior staff member suddenly drives a brand-new car. (ii) A modest salary earner starts vacationing in Dubai with the whole family. Not Jinja. Not Fort Portal. But to Dubai. Emirates. Burj Khalifa. Floating breakfast. All in full HD on their WhatsApp status. (iii) Let us be honest. You know your colleague’s payslip. You all queue at the same salary office. Then out of nowhere, this person shows up driving a car whose logbook is allergic to salary loans. He says it is “God’s blessing.” Yet even God is whispering, “My child, do not drag me into this one.” When you see lifestyle levitate while the pay grade remains grounded, do not clap. Do not borrow style. Ask: What is funding this miracle? Because when fraud happens, the red flag is not the theft. It is the silence and side-eyes from colleagues who pretend not to notice. And by the time HR wakes up, the car is sold, the Dubai album is complete, and the audit trail is colder than your office tea. I always tell people that do not envy what you do not understand. Fraud always looks like success until the handcuffs come. 2) Unwillingness to take leave (i) Fraudsters guard systems like gold mines. You would think their password is their blood type. (ii) They fear exposure, not sunburn. If someone else logs in while they are away, the secrets start coughing. (iii) When someone refuses annual leave for five years straight, claiming they “just love working,” do not applaud. Raise the alarm. Let me paint you a picture. Peter in Accounts has not taken leave since Museveni last reshuffled the cabinet. Every year, HR begs him: “Please go and rest.” He smiles, declines, and somehow still gets his leave allowance. But here is the trick: Peter is not hardworking. He is hard to hide. His Excel sheets have more formulae than a PLE math paper. He reconciles his books, approves his payments, and sends his audit responses. Ask to sit at his desk? “Ah, boss, my work is a bit sensitive.” Sensitive indeed. The last guy who insisted on relieving him? Transferred to stores. When a staff member treats leave like a death sentence, they are not loyal. They are laundering. Remember, everyone needs rest. But a fraudster? They can not afford it. Their scheme collapses the moment someone else logs in. Audit tip: If someone resists delegation like it were a crime, check. It probably is. 3) Over-familiarity with vendors (i) Personal friendships become procurement shortcuts. “I know a guy,” they say, and that guy always wins. (ii) One supplier keeps getting the deals even when they quote higher, deliver late, or write invoices like riddles. Why? Because he buys the drinks and sometimes the fridge too. (iii) That “drink after work” culture? It is not networking. It is onboarding into a kickback scheme. Let us unpack this. Meet Sharon from procurement. Friendly. Efficient. Always available. Her best friend, Brian, owns “B-Tech Supplies.” Every tender? He wins. Every evaluation? He scores 98%. One time, his quote arrived in PowerPoint instead of Excel. Still awarded. Why? Because Sharon and Brian have a rhythm. You will find them every Friday at Cayenne laughing like business is a comedy. But what is not funny is how B-Tech delivers reams of paper that vanish faster than the toner. Ask Sharon for a justification report, and she replies, “Trust me, Brian is reliable.” That’s not due diligence. That is due to fraud. Real suppliers compete. Fake ones collude. If one vendor keeps winning while everyone else is just ‘for formality,’ you are not running procurement. You are hosting a reunion. Friends do not let friends win tenders. At least not without proper evaluation, clear documentation, and a firewall between social life and supplier lists. Because when vendors and staff are this cozy, what is being supplied is not just stationery. It is a scandal. 4) Excessive control over processes (i) One person handles everything: initiation, approval, reconciliation. (ii) That is not efficiency. That is fraud in stealth mode. (iii) Segregation of duties exists for a reason. Now, meet Sarah. The finance admin at a vocational institute in Wakiso. On paper, she was a miracle worker. Initiated payments, approved them, updated the ledger, and even printed the cheques herself. The Principal used to praise her: “Sarah is very reliable. Does not disturb anyone.” Exactly. Because disturbing people brings witnesses. When the internal auditor finally got access to her files, they found something strange. The same stationery supplier had invoiced the same items four times in a quarter. Toner. A4 paper. USB flash drives. Same descriptions, same amounts, just different invoice numbers. Turns out, Sarah had been processing and paying ghost suppliers. But since she reconciled the books herself, it always looked clean. Until a sick day exposed her empire. A colleague covering for her asked one innocent question: “Why are we paying UGX 4 million for ‘flash disks’ every month?” That is when the curtain dropped. The fraud had been running for 3 years. Estimated loss? UGX 212 million. One-person processes are not a strength. They are a system failure. Segregation of duties is not a bureaucratic nuisance. It is your first line of defense. When one person controls every step, audit trails vanish, checks collapse, and fraud moves in quietly, confidently, and with receipts. 5) Missing or suspicious documentation (i) Ghost receipts. (ii) Repeated ‘lost’ files. (iii) Frequent ‘technical errors’ in audit trails. Classic cover-up tactics. Now
The fraud diamond: How good people cross the line
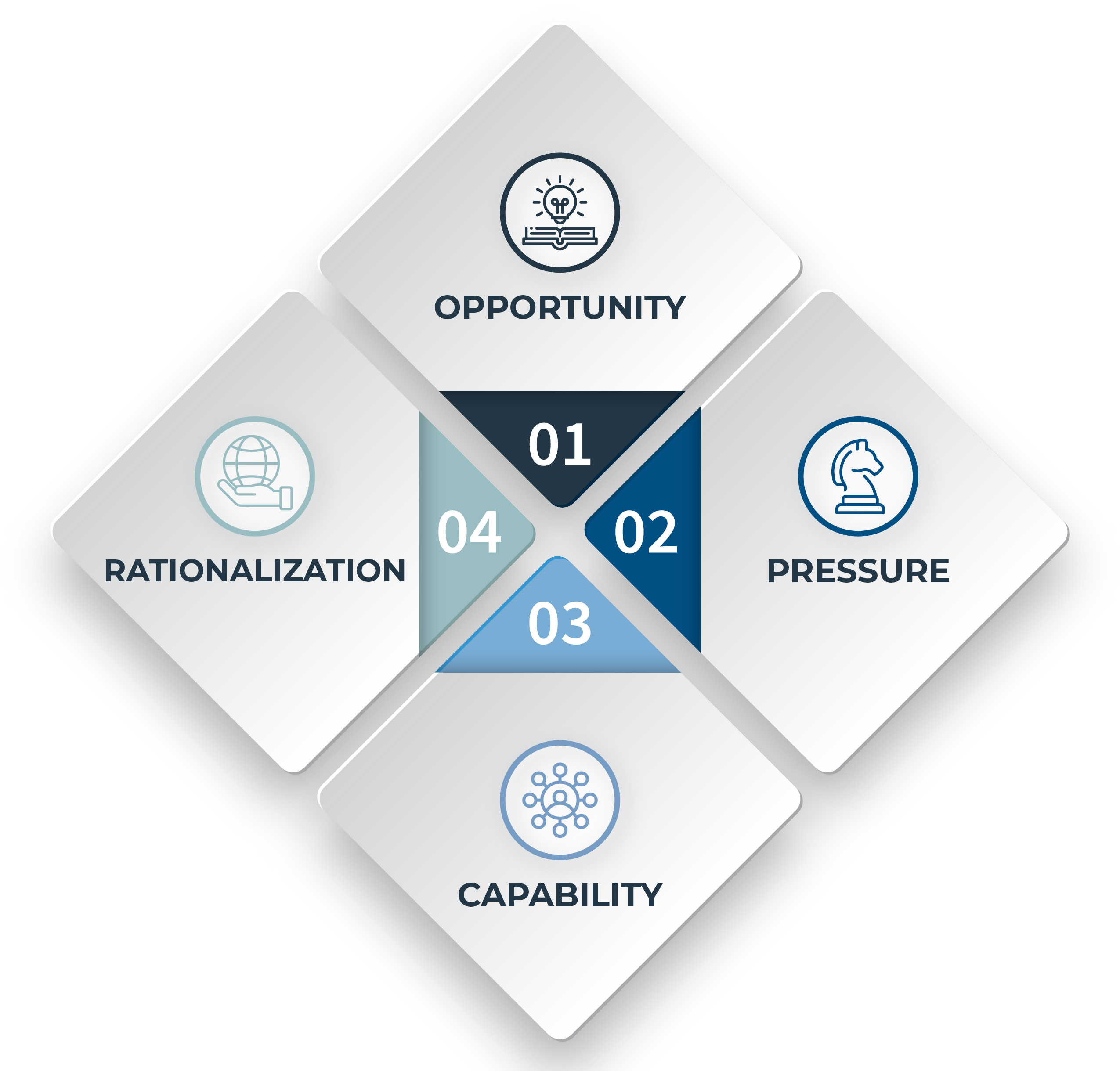
Fraud doesn’t begin with bad people. It begins with pressure. With a quiet “just this once.” With a system that looks away. To truly understand how fraud happens, forget the Fraud Triangle. That’s kindergarten. Step up to the Fraud Diamond, a sharper, more dangerous model. It exposes not just why fraud occurs, but how the fraudster pulls it off. There are four points to this diamond. Each one cuts deeper. 1) Motivation or pressure – the fire under the pot I call it the boiling kettle. Pressure builds in silence. It could be school fees, a sick parent, a gambling habit, or a toxic bonus structure. Inside, the kettle starts to boil. If there’s no ethical outlet, no support system, the steam seeks escape. In one case in Mbale, a payroll officer altered the system to pay herself “advances.” Why? Her landlord had given a final eviction notice. Her children’s school threatened suspension. In her head, this wasn’t theft, it was survival. Just last Saturday, I was sitting in a restaurant having a meal when a man suddenly shouted at the top of his voice: “James, you’re a very bad person. I’m coming to evict you tomorrow. How do you live in someone’s house for over ten months without paying a single coin? I borrowed money to build that house, I pay URA, I pay KCCA, and even the man who opens the gate for you—but you sleep there, produce children, and don’t even think about paying rent? What kind of man are you? How do you even find the energy to get in the mood for producing children with that ever-accumulating rent hanging over your head?” The man, clearly the landlord, was furious and didn’t allow the tenant to say a single word. That, my friend, is pressure. Now imagine that same tenant works in your company… and has access to money. 2) Opportunity – the unlocked window A window left open at night gives easy access to intruders. Pressure alone doesn’t cause fraud. Opportunity invites it. Weak controls. No supervision. Poor segregation of duties. In most district local governments, fuel fraud thrives because no one reconciles fuel cards against mileage and journeys. No trackers. No oversight. So drivers inflate trips. Storekeepers divert fuel to boda riders. The window is open, and the thief doesn’t even need to break in. 3) Rationalization – the bedtime story When a thief believes s/he’s the hero, smiles while stealing! To sleep at night, fraudsters tell themselves stories. “They owe me.” “It’s just a loan.” “Everyone does it.” “I have worked for this company for too long, I deserve this!” In Gulu, a hospital accountant stole UGX 75 million over 3 years. He told investigators, “I was just reclaiming all the weekends I worked without pay.” That’s not a justification—it’s a confession wrapped in entitlement. 4) Means – the master key Before you make that spare key, make sure your locksmith has good morals. This is what the traditional fraud triangle missed. You can have the motive or incentive or pressure, the chance or opportunity, and the excuse or rationalization but without the means, you’re still locked out. Means are the skills, access, and tools to execute fraud. System access. Insider knowledge. Technical know-how. In Wakiso, an IT assistant cloned mobile money withdrawal codes after observing the finance team for months. No one suspected him until one day, UGX 210 million vanished from a project account. The complete diamond motive, opportunity, rationalization, and means. If you want to stop fraud, don’t just audit. Don’t just preach ethics. Break the diamond. Remove the pressure by offering support. Start personal finance training, family planning talks, and staff mentorship programs. Shut the window by tightening the controls. Separate duties, enforce approvals, and audit surprise transactions regularly. Challenge the stories people tell themselves. Teach ethics through real-life case studies and promote an open, values-driven culture. Block the tools they need to act. Limit system access, rotate roles, and monitor user activity with alert systems. Fraud isn’t magic. It’s mathematics. Fix the equation before it breaks you. And now you know the formula.
Don’t be the next headline: 5 simple steps to prevent fraud today
Fraud doesn’t knock. It walks right in through your open doors, process gaps, ignored red flags, and blind trust. And when it hits, it hits hard. Reputations ruined. Careers ended. Cash gone. Before you become the next cautionary tale, here are IFIS’s five practical steps to block the fraudster’s path starting now. 1) Segregate duties If one person controls initiation, approval, and payment, you’ve built a perfect fraud machine. Split roles. Always. No one person should control an entire transaction process. This includes payroll, procurement, and reconciliations. In Ugandan SACCOs, for example, we’ve seen treasurers process fake withdrawals for non-existent members simply because no one else was checking. 2) Verify before you trust Your most trusted employee could be your biggest threat. Do independent verifications, especially for suppliers, ghost staff, and “urgent” payment requests. Call back. Confirm. Don’t assume. That “vendor” might be your staff using a cousin’s bank account. 3) Monitor your logs System logs don’t lie, but only if you review them. Watch for late-night logins, multiple failed password attempts, or sudden system changes. Many fraud cases begin after hours when no one is watching. Install alerts. Review them weekly. 4) Rotate responsibilities Never let one person own a role for years without a break. Fraud loves routine and familiarity. Make leave mandatory. Rotate roles periodically. That alone exposes long-running schemes. A cashier’s theft was only discovered during maternity leave in one Eastern Uganda district. 5) Train everyone Fraud is not just an IT problem. It’s a people problem—train staff to spot social engineering, phishing emails, and manipulation tactics. Make fraud prevention part of onboarding and annual refresher training. When everyone is alert, the fraudster is isolated. Final word: Fraud isn’t just a finance problem. It’s a leadership failure. Fix the culture. Build systems. And for heaven’s sake, stop relying on trust alone. Trust is not an internal control. Stay alert. Stay protected.
Our pentest approach. Why most risk management teams are NOT future ready
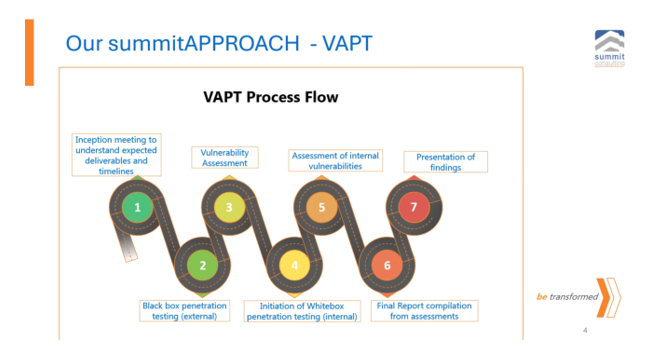
You have a penetration testing process. You have a risk management department. You have an internal audit team. Yet you are still vulnerable. Why? Because most teams are not evolving as fast as the threat landscape. At Summit Consulting, our VAPT approach is simple and brutal: Inception meeting: Define timelines, expectations, and failure points up front. Blackbox penetration testing: Simulate a real-world external attack without insider knowledge. Vulnerability assessment: Identify cracks before the enemy does. Whitebox penetration testing: Simulate insider threats with full access. Internal vulnerabilities assessment: Your weakest links are always inside. Final report compilation: No sugar-coating. Just the truth. Presentation of findings: Executive-level intelligence, not geek talk. Here’s the real question Are your internal audit and risk teams evolving to meet today’s threats? Or are they still stuck writing yesterday’s audit checklists? Cyber risk is not a compliance exercise anymore. It is a survival strategy. Why most risk management teams are not future-ready In 2024, a mid-sized Ugandan financial institution asked us for a routine vulnerability assessment. They had just passed a regulatory audit with flying colours. Their internal audit team had ticked all the boxes. We applied our summit iShield 7-step VAPT approach. Inception meeting: Their IT head assured us, “We’re clean. Just do a quick scan.” Blackbox testing: Within 4 hours, we breached their email gateway and sat silently inside their network. Vulnerability assessment: Found 47 high-risk exposures, including default admin credentials on core switches. Whitebox testing: Gained domain admin privileges in less than a day, with full access to their backup systems. Internal vulnerability check: Discovered weak passwords like “Welcome@123” and unpatched ERP servers. Final report: We drafted a 54-page red alert report with proof-of-exploit screenshots. Board presentation: Their CEO nearly fell out of his chair. His exact words were: “But our IT team said we were safe?” Here’s the reality Their internal audit team had never tested controls, only reviewed paperwork. Their risk team didn’t even understand what a lateral movement attack was. That is the problem. Too many organizations are blind, not because they lack talent, But because they confuse compliance with security. They are auditing locks, not testing doors. Our VAPT approach is not just a scan, it’s a war game. If your internal experts can’t handle simulated attacks, how will they survive real ones? Now is the time to partner with experts who can support them to add value. Future-ready internal audit and risk management team, outsource the cybersecurity assurance services to an external firm, so that they do not move blindly. Leadership takeaway Compliance passed. Pen test failed. Only one of those outcomes protects your business. Wake up. Test. Transform. Contact us today to be your partner. Visit www.summitcl.com. #RiskManagement #InternalAudit #CyberSecurity #VAPT #BeTransformed #MrStrategy
Fraud happens in silence: Speak up, Save millions
On 11th February 2025, a procurement officer at a prominent government parastatal in Entebbe signed off an “emergency” UGX 360 million payment for the supply of solar panels. No panels arrived. No alarm was raised. No questions were asked. By June, after seven similar “emergency procurements,” over UGX 2.7 billion had quietly disappeared. Nobody saw. Nobody heard. Nobody dared to speak. Until one junior stores clerk, earning UGX 800,000 a month, finally blew the whistle anonymously. Summit Consulting Ltd was contracted to investigate, weeks after internal damage-control efforts failed spectacularly. By then, the silence had cost them dearly. Culture versus Compliance Most Ugandan organizations boast thick policies, glossy codes of conduct, and colorful posters urging integrity. But when fraud happens, real culture shows. At this parastatal, the culture was loud in meetings, but dead silent when it mattered. Staff had seen inflated invoices. They had noticed the rushed LPOs. But speaking up meant isolation. Transfers to Karamoja. Career death. So they shut up. Until it was too late. How the fraud was perpetrated a) Emergency procurement loophole i) “Emergency” procurements bypassed standard competitive bidding, based on fictitious justifications like “urgent rural electrification.” ii) Dummy suppliers, registered two months prior, were awarded contracts. iii) Payments were made before delivery, with fake site inspection reports signed off by internal colluders. b) Covering the tracks i) Manual alteration of bid committee minutes to reflect fake evaluation processes. ii) Destruction or loss of key procurement files under the guise of office “renovations.” iii) Coordination with rogue internal auditors to delay review cycles. Money movement details a) 65% of stolen funds were withdrawn in cash within 48 hours of payment disbursements from the institution’s account. b) 20% was layered through school fees payments, and land purchases in Wakiso and Mukono registered under third parties. c) 15% was used to pay off insiders and fund a political “war chest” in anticipation of the 2026 elections for a local MP. By the time we traced the money, a full recovery was nearly impossible. Red flags ignored a) Repeated emergency procurements from the same five “suppliers.” b) Payment schedules consistently just below the UGX 500 million threshold requiring higher level scrutiny. c) Frequent staff reshuffles of whistleblowers and critical thinkers. Our investigation methodology a) Deep dive procurement audit We requested original procurement files and compared them with system records, uncovering material inconsistencies. b) Lifestyle forensics We profiled suspected staff: unexplained new houses, fancy SUVs, and unexplained “business investments” by spouses. c) Anonymous tipline deployment We set up a confidential reporting platform, receiving over 37 insider tips within one month painting the full picture of the syndicate. Challenges faced a) Fear culture Even after formal whistleblower protection was assured, most staff still hesitated to testify without heavy anonymization. b) Legal bottlenecks Prosecution processes dragged due to weak evidence preservation and political interference. c) Record tampering Several key files and emails mysteriously “disappeared” during the early days of the investigation. Confirmed loss: UGX 2,720,450,000. Projected indirect loss: Another UGX 4 billion in opportunity costs, reputation damage, and donor sanctions. Fraud thrives in silence. Fraud lives because honest people fear. Fraud wins because organizations punish candor more than they punish theft. If your staff fear HR more than they fear a court of law, your institution is one tender document away from collapse. If you truly want to save millions, build a culture where speaking up is rewarded not buried. Uganda’s biggest frauds are not committed by masterminds. They are committed by mediocres shielded by fear, enabled by silence. Fraud is not a financial risk. It is a cultural cancer. Kill the silence, or the silence will kill your organization.