
Every time you click a suspicious link, share your email on a shady site, or use the same password across...

Every time you click a suspicious link, share your email on a shady site, or use the same password across...

Welcome to the test that separates the cyber-savvy from the cyber-sloppy. You may think you’re safe. You don’t click on...

It started like any other Monday. Overcast skies. Heavy traffic on Jinja Road. At 9:13 AM, the IT manager of...

It arrived at 8:47 AM. Subject line: “URGENT – Unpaid Invoice Attached.” To most people, it looked ordinary. To Susan,...

Think you can trace digital footprints, uncover hidden evidence, or spot cybercrime like a pro? Take this quick but revealing...

The war room is an interesting place – you get to see everything in action. The iShield360 cybersecurity center monitors...

It all starts with a compromise It always begins with a password. In June 2024, a procurement officer at a...
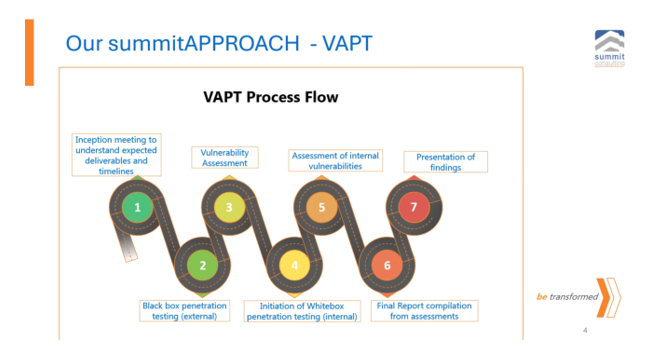
You have a penetration testing process. You have a risk management department. You have an internal audit team. Yet you...

A padlock on a chicken coop means nothing if the fox has the keys. In a recent cybersecurity audit, we...

The first thing they stole was time. For nearly two years, a group of insiders siphoned money from the bank,...

we specialize in bridging the gap between knowledge and application.


© 2025 All rights reserved Institute of Forensics and ICT Security | IFIS is the training arm of Summit Consulting Ltd